How to Implement Shift Left in DevSecOps

Shift-Left is a development approach that addresses security issues early in the development lifecycle. Integrating security practices from the beginning ensures that potential vulnerabilities are identified and mitigated early, reducing the cost and effort required to fix them later.
In this approach, security is no longer a bottleneck that delays software release but an organic part of the development process. Recent data highlights the necessity and benefits of this approach. According to Datadog's State of DevSecOps 2024 report, many organizations are not fully embracing shift-left principles and automation for securing cloud deployments, leading to security vulnerabilities and data leaks. In this article, we go over tangible steps companies can take to make shift-left an inseparable part of their processes.
1. Spread the word about Shift-Left
A Shift-Left culture begins with training sessions to educate developers and teams on the critical importance of shifting security left and its benefits to the development process. Ensure that developers, testers, operations teams, and security professionals understand their roles in integrating security throughout the software development lifecycle. Use workshops and cross-functional collaboration sessions to reinforce these concepts.
2. Integrate Security into Development
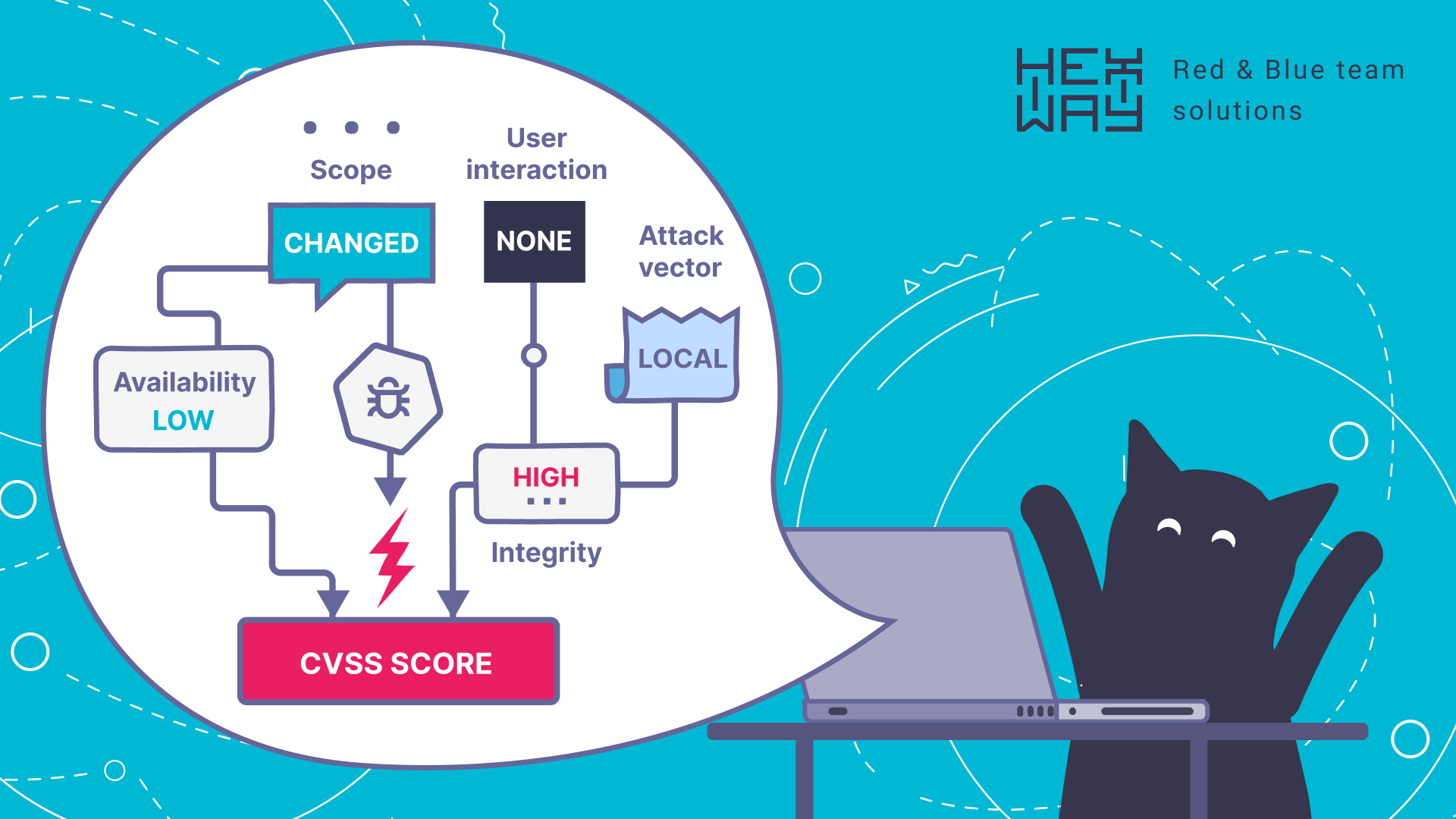
Embed security practices into key development workflows, such as code reviews, design reviews, and requirements gathering, to identify and mitigate vulnerabilities early. Provide developers with the necessary training and tools to adopt secure coding practices. Automating and prioritizing security tasks is vital because it streamlines the development process, reduces manual errors, and promptly addresses critical vulnerabilities. Many automation solutions help with these activities, making the development process faster and solving the security bottleneck issue. One such solution is Hexway ASPM, which automates vulnerability detection and prioritization, integrating with CI/CD pipelines to facilitate early detection and remediation of security issues, focusing on the secure software development lifecycle (SSDLC).
3. Automation is the key
Implement advanced security testing methods, such as static application security testing (SAST), dynamic application security testing (DAST), and software composition analysis (SCA). These automated tools should be integrated into the CI/CD pipeline to ensure code and dependencies are scanned for vulnerabilities during the build process.
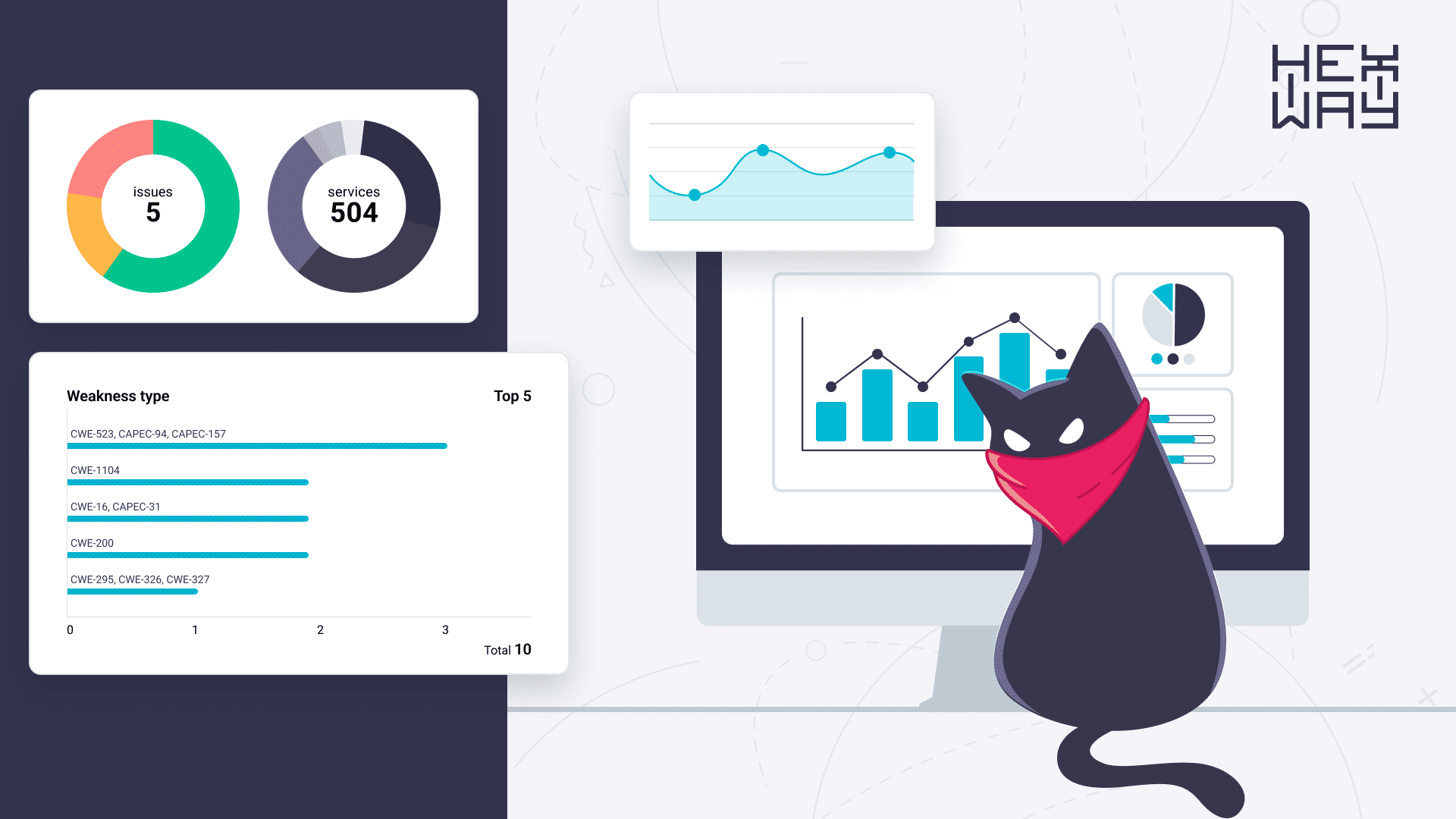
Security testing generates a lot of security data, which is often noisy and challenging to sift through without proper parsing and normalization. Solutions like Hexway ASPM are helping with this as they aggregate outputs from various scanners, normalize data, and deduplicate findings. This process not only simplifies and speeds up the identification of security issues but prioritizes vulnerabilities based on severity, enabling efficient remediation and quick task addressing.
4. Integrate Security Early in Testing
Integrating security testing within unit and integration tests is essential to identify vulnerabilities early in the development cycle. Shifting the security focus to the development phase reduces the number of vulnerabilities that could appear in production and minimizes the costs and complexities associated with late-stage remediation.
This proactive approach ensures a more secure product and avoids expensive fixes post-release. This embodies the Shift Left approach, i.e., fixing vulnerabilities before production.
Security scanning generates a lot of noisy data, which is very hard to go through without additional parsing and normalizing solutions. Sometimes, regular parsing helps, but it only helps with parsing; in the end, you still won't be able to answer important questions like what to fix first. Solutions like ASOC or Hexway ASPM help with data normalization and aggregation, simplify vulnerability prioritization based on severity score, and automate issue deduplication to speed up security fixes.
5. Adopt Infrastructure as Code (IaC)
Leverage Infrastructure as Code (IaC) to define programmatically and provision infrastructure resources. Implement robust security controls and best practices within your infrastructure code, including enforcing least privilege access, network segmentation, and automated security configurations.
6. Continuous Monitoring
Continuous monitoring reduces the number of vulnerabilities in the final product or update. This is especially crucial when managing multiple products, services, or updates simultaneously. Monitoring applications and infrastructure in real-time is important to instantly detect and respond to security threats. Gather telemetry data, logs, and metrics to gain deep visibility into system behavior and quickly identify security incidents.
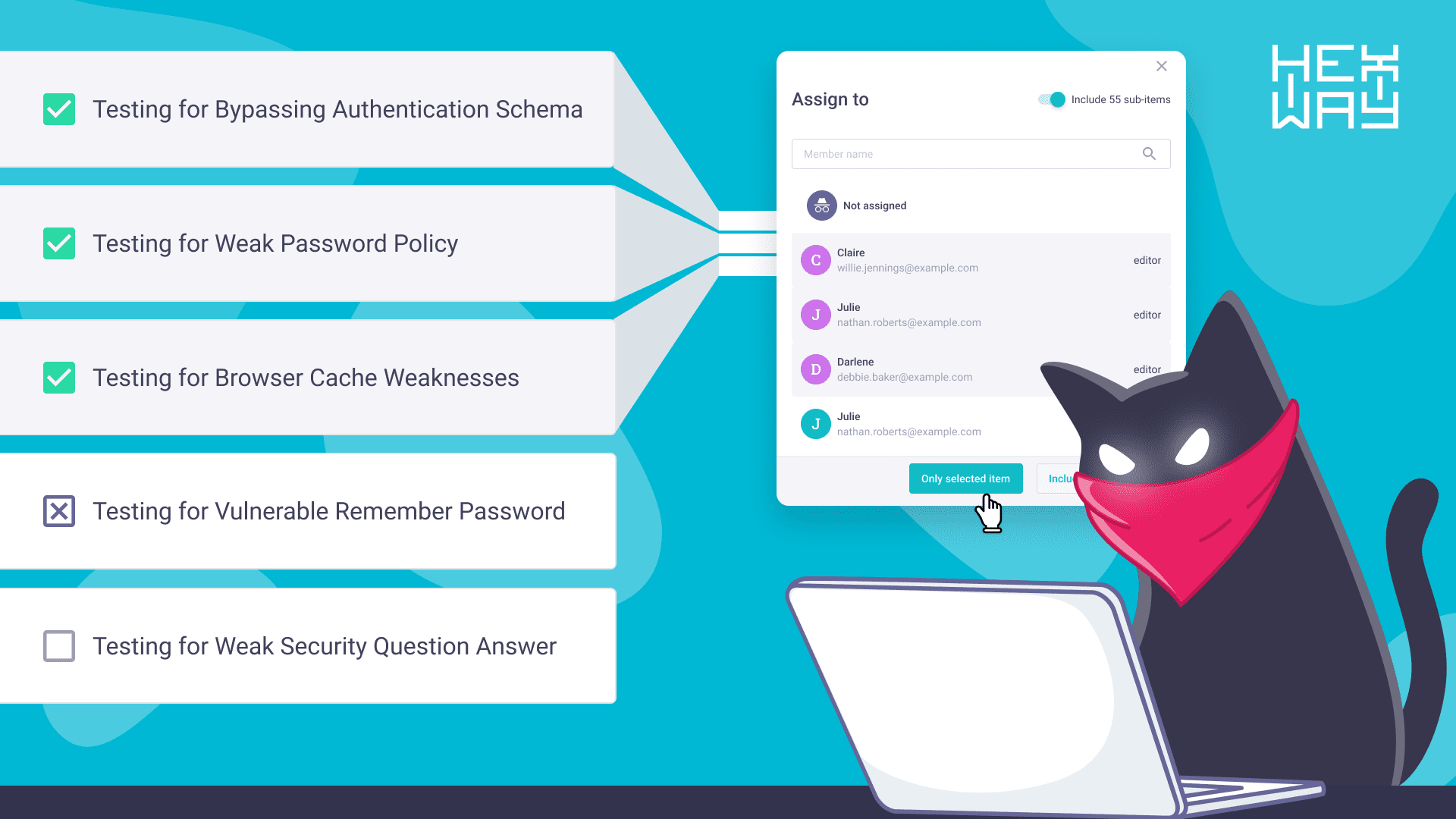
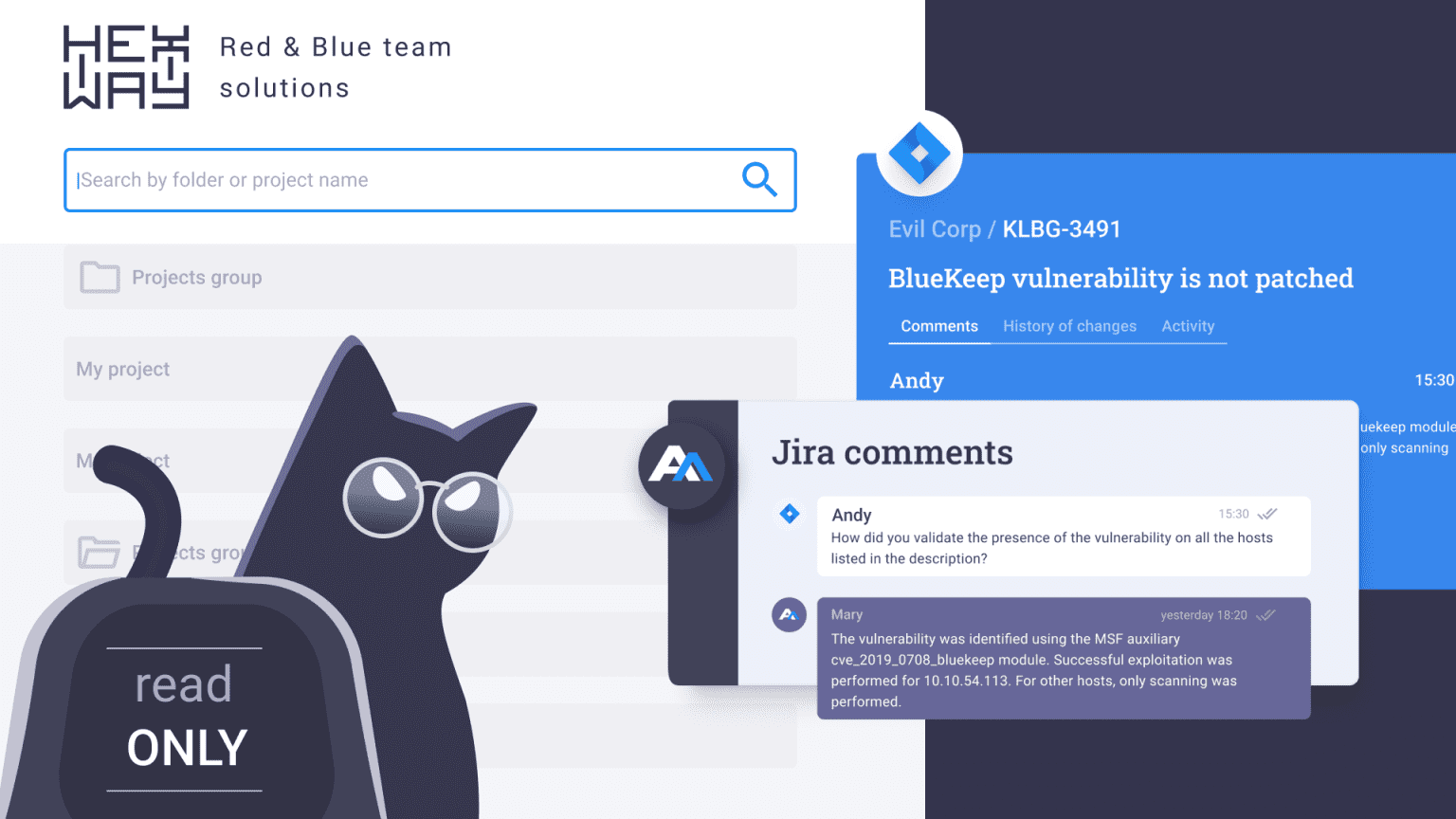
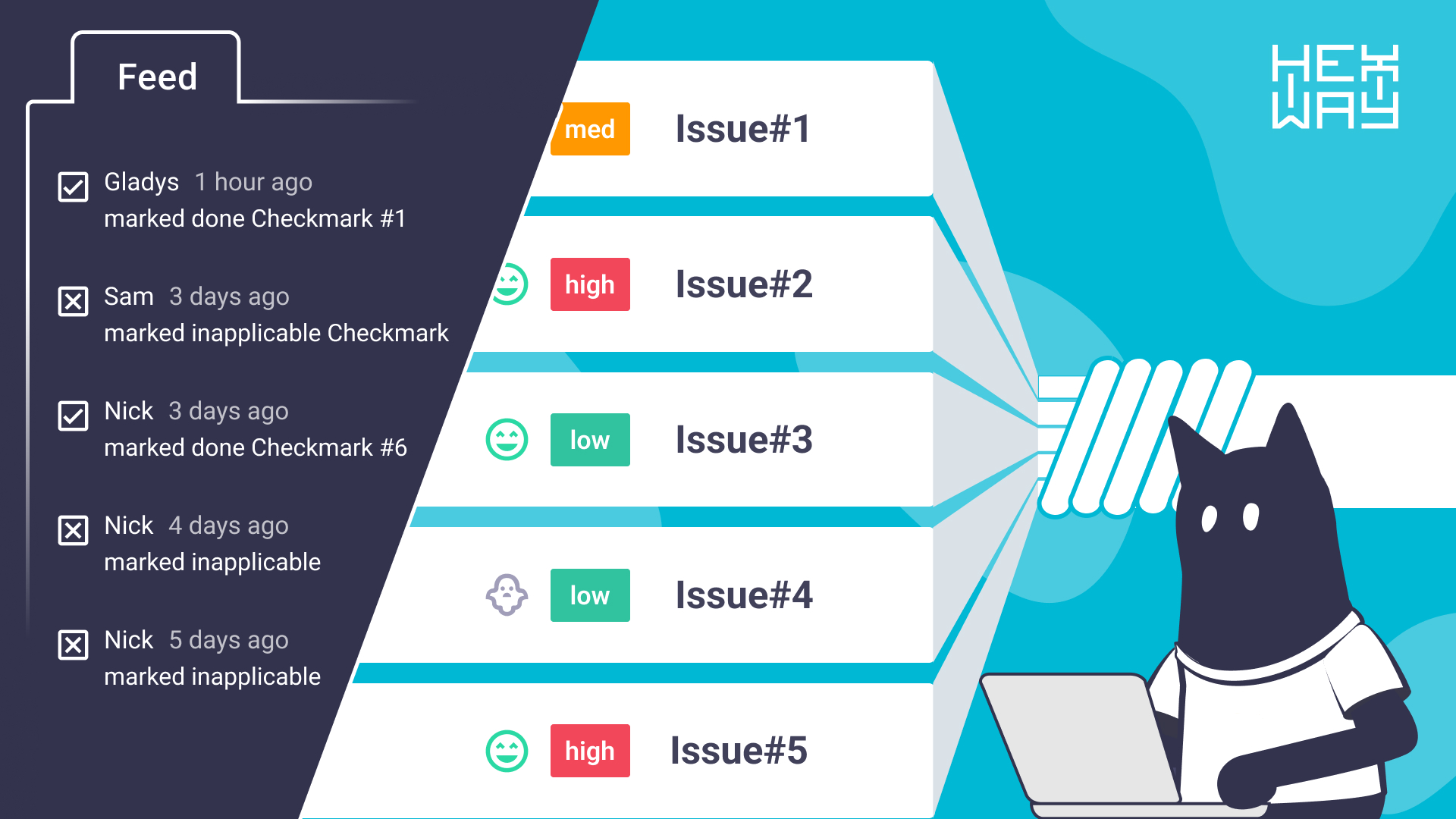
At this stage, vulnerability management platforms are required to help security teams track new vulnerabilities and directly address them with deep VCS integrations. These integrations provide detailed information on the vulnerable code parts, including the commit author, commit history, and related code changes.
7. What about communication?
Strengthen collaboration and communication between development, operations, and security teams to align security objectives and priorities. Promote regular meetings, cross-functional training sessions, or even beer pong parties to build a shared understanding of why sharing information with colleagues is important and support transparent communication.
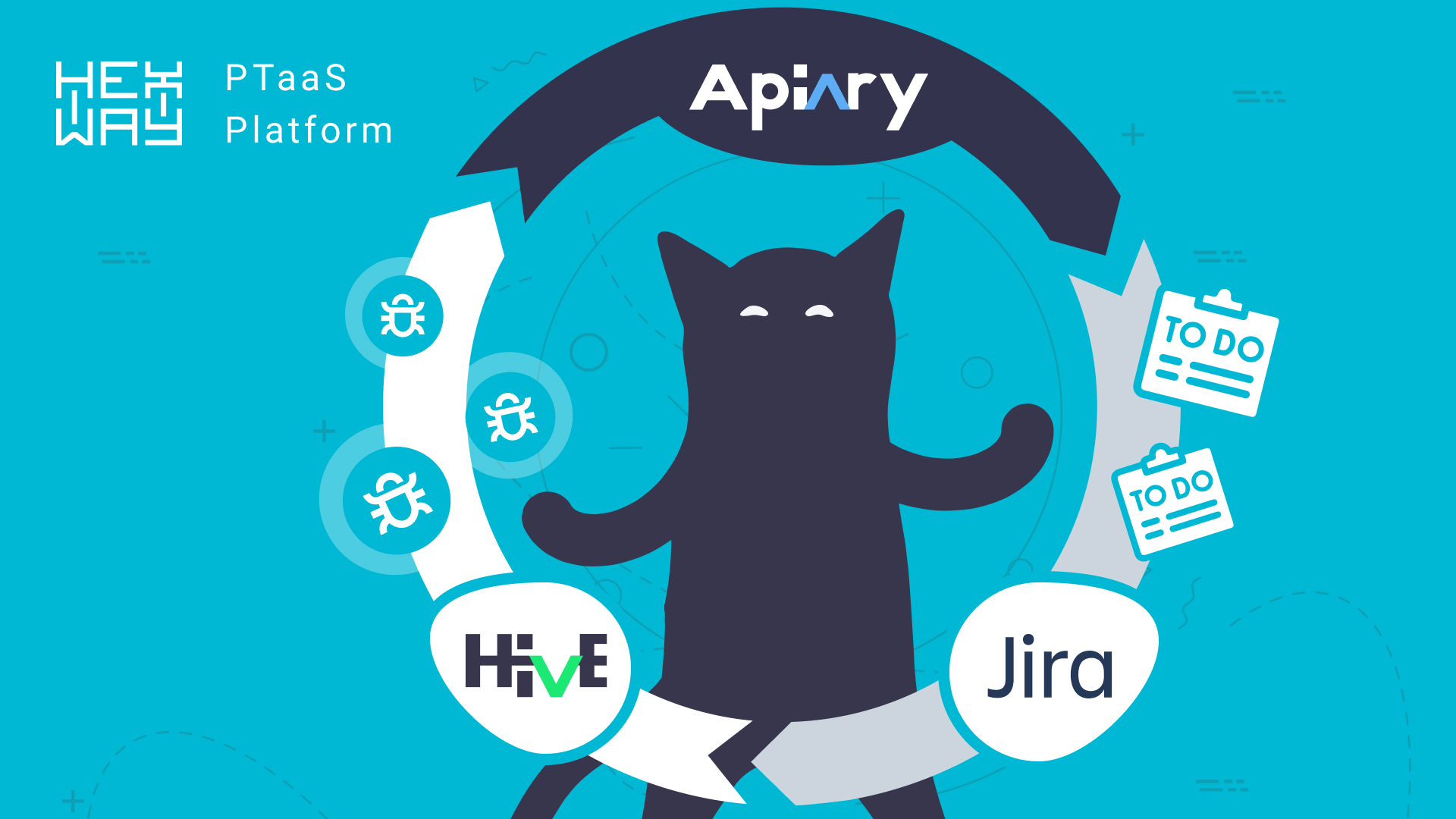
Communication is often a stumbling block in many IT companies, with issues like forgotten updates or unchanged ticket statuses leading to missed vulnerabilities or even data leaks. This is especially important when working with developers. With that in mind, Hexway ASPM unifies remediation control processes and integrates with popular tools like Jira for fast task tracking and communication.
Vulnerability management platforms sometimes include bidirectional integrations: security teams get updates on the issues, and developers receive new tickets for fixing issues. This scheme makes the fixing process transparent and accessible for all team members, ensuring a coordinated and effective response to security challenges.
8. Be Ready to Meet Regulations
Embed compliance and governance requirements into the development process through robust security policies, standards, and controls. Automate compliance checks and audits to ensure that applications and infrastructure meet regulatory requirements and industry best practices.
Hexway ASPM assists companies in meeting their regulatory and compliance needs by facilitating the shift-left approach. This methodology ensures that security and compliance are integrated early in the development lifecycle, and Hexway ASPM is an intelligent, SSDLC-focused tool that supports this proactive approach.
By implementing the steps outlined in this article, organizations can effectively adopt the shift-left approach in DevSecOps. This strategy enhances the security posture of their applications and infrastructure while accelerating the delivery of secure and reliable software.
Hexway ASPM is a universal tool that helps companies Shift Left in their development and security processes by automating manual parsing, deduplication, task creation, and other security operations. This allows security and development to focus on what matters — finding and fixing vulnerabilities before they hit the prod.
It focuses on the company's needs with a flexible, user-friendly approach and great performance metrics, distinguishing Hexway ASPM from most open-source and paid solutions.
Please don't hesitate to try out Hexway ASPM's community version to see how Shifting Left can be painless and free.