0.62. New filters, new MD hotkeys, security patches and more

Version 0.62 of the Hexway Pentest Suite brings advances in security precision and documentation clarity for both Hive and Apiary products.
New in Hive
New filtering in Project Data. One notable improvement is the refined filtering. We've moved from simple string comparisons to intelligent version analysis for targeted vulnerability identification. This new feature helps identify vulnerabilities in third-party services, making it easier to secure the network against various CVE threats.
For example
service.product == "Apache httpd" and service.version >= "2.4" and service.version <= "2.4.52"
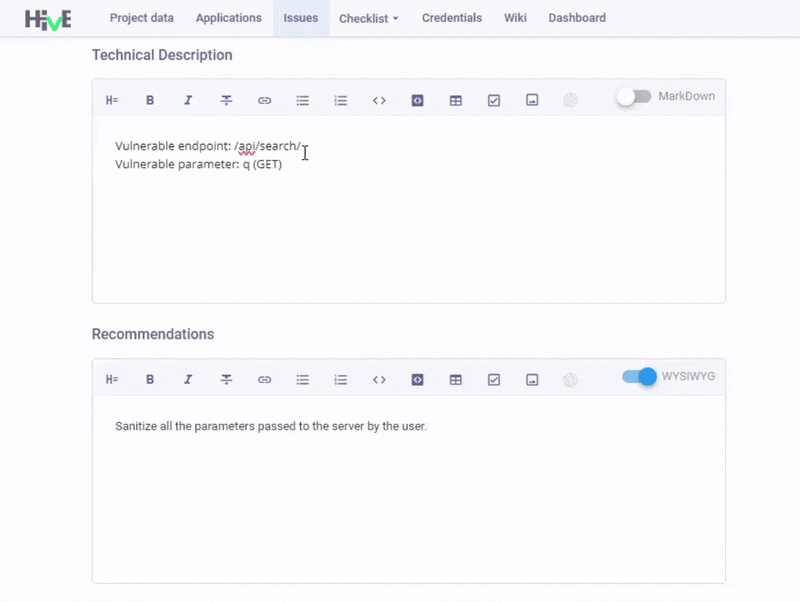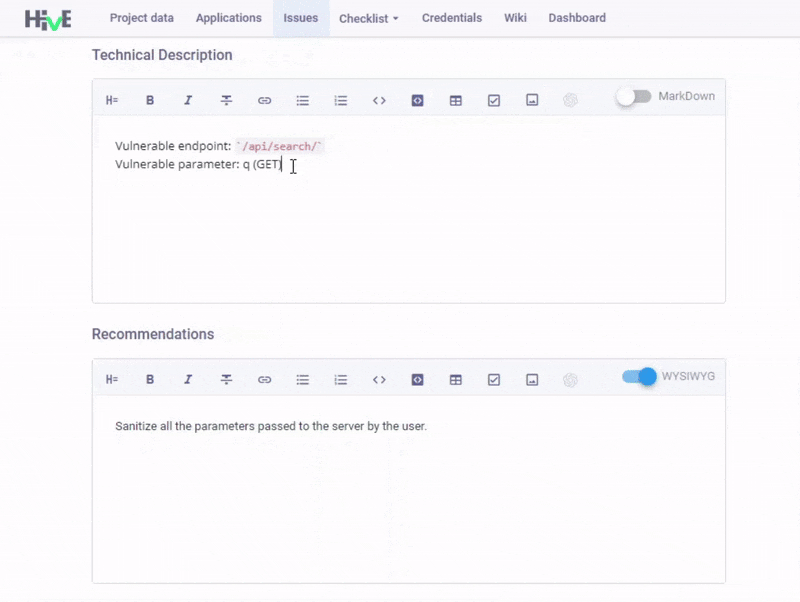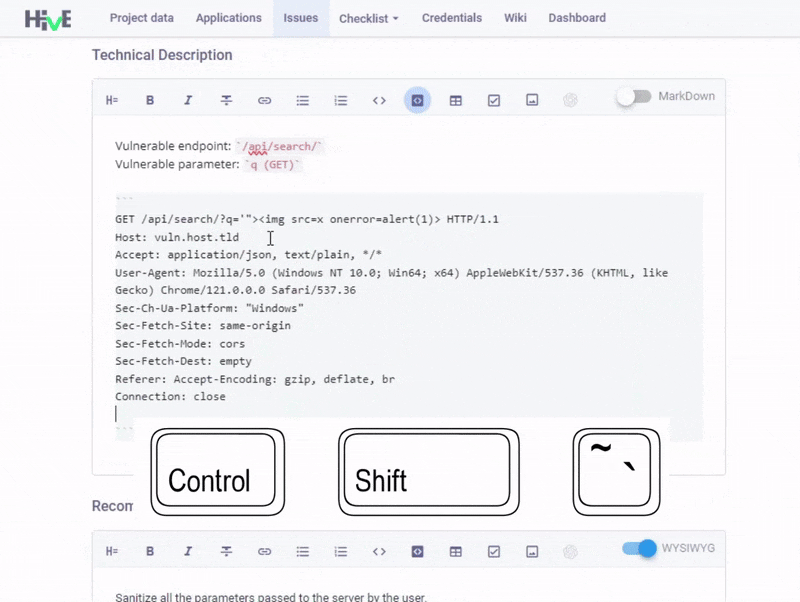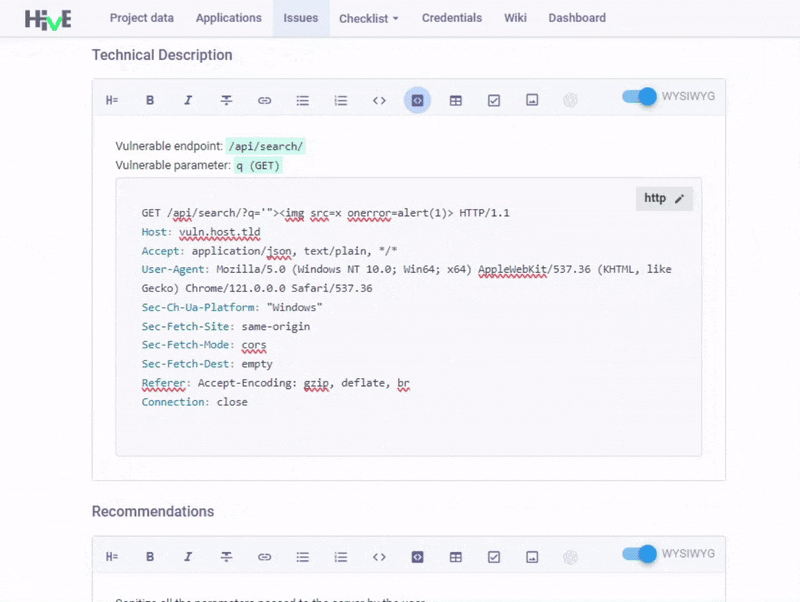
Hotkeys in MD editor. Another awaited update is the hotkeys and syntax highlighting in Markdown Editor. We've fixed the code snippet display issues and added new hotkeys (Ctrl+` for inline code and Ctrl+Shift+` for code blocks) to speed up formatting tasks. We've also introduced syntax highlighting in code blocks to produce documentation that is not only accurate but also visually accessible.
Key features
- Version Filtering: Target vulnerabilities more accurately with advanced filtering capabilities.
- Markdown Editor Updates: Improved code section display, new hotkeys, and syntax highlighting for clearer documentation.
- Navigation and Management: Updated project list with suggested features and a more comprehensive view of recent projects.
- Optimized Issue Management: Increased chunk size for issue retrieval to efficiently handle extensive amounts of data in large projects.
New in Apiary
Checklist Execution and Display. The update introduces improvements to the synchronization and display of results, making the process of working with checklists more intuitive and efficient.
User Groups for Leveled-up Collaboration and Security. The introduction of user groups allows users to be separated into groups with restricted visibility. This provides a high level of privacy and security, allowing different clients to work within a single Apiary instance without interacting or even being aware of each other.
More improvements
- Fixed Issue Assignment Bug. A bug that prevented users from assigning issues to users already added to the project or themselves has been fixed, increasing the flexibility of task management.
- Docx Generation Improvements: We've fixed the behavior of numbered lists in docx files, ensuring seamless integration of images without disrupting list formats.
- Refined Filter Functionality: This update resolves unexpected behavior in tag-based filter selections, improving the accuracy of data retrieval.
- UI fixes: Issues with UI collapse when using PgUp/PgDn in the Issue Editor and unnecessary line breaks in rendered lists have been addressed, providing a more intuitive navigation experience.
- Wiki Page Navigation: Switching between wiki pages containing tables is smoother, with improvements to prevent content overflow.
- Security Patches: We've updated internal services to the latest versions, mitigating a wide range of vulnerabilities identified by CVE codes*, such as CVE-2023-29159, CVE-2023-4039 or CVE-2024-22365, strengthening our platform's defenses against potential threats.
Stay up-to-date with emerging pentest challenges by this update and take advantage of these state-of-the-art features. Upgrade now to discover these enhancements or try the latest version for free.
*Full list of fixed vulnerabilities in internal services: CVE-2023-29159, CVE-2023-2975, CVE-2023-31437, CVE-2023-31438, CVE-2023-31439, CVE-2023-31484, CVE-2023-31486, CVE-2023-3446, CVE-2023-36054, CVE-2023-37276, CVE-2023-3817, CVE-2023-4039, CVE-2023-43804, CVE-2023-4527, CVE-2023-45803, CVE-2023-4641, CVE-2023-47038, CVE-2023-4806, CVE-2023-49083, CVE-2023-4911, CVE-2023-52323, CVE-2023-5363, CVE-2023-5678, CVE-2023-5752, CVE-2023-5981, CVE-2023-6129, CVE-2023-7008, CVE-2023-7104, CVE-2024-0232, CVE-2024-0553, CVE-2024-0567, CVE-2024-22365












