Latest researches about founded vulnerabilities and how you can try to play with them
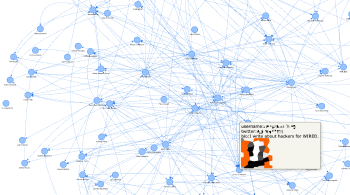
The short story about Clubhouse user scraping and social graphs
TL;DR During this RedTeam testing, we used Clubhouse as a social engineering tool to find out more about our client's employees. UPDATE: While we were preparing this article for publication, ...

r00kie-kr00kie. Exploring the kr00k attack
TL;DR We created and published a PoC exploit of the kr00k attack (CVE-2019-15126): https://github.com/hexway/r00kie-kr00kie All technical details can be found in the Process section. INTRODUCTION AND MOTIVATION In February 2020, ...

Piercing the Shield. Breaking the FunctionShield cloud security library
TL;DR We've found a vulnerability in FunctionShield, a cloud security library, that allows bypassing its tightest restrictions completely. All technical details can be found in the "Process" section. Cloud computing ...

Apple bleee. Everyone knows What Happens on Your iPhone
Users value their privacy, and Apple understands that. We even see related PR activities. "What happens on your iPhone, stays on your iPhone." Let's see if it's true. TL;DR If ...






