TL;DR
During this RedTeam testing, we used Clubhouse as a social engineering tool to find out more about our client's employees.
UPDATE:
While we were preparing this article for publication, cybernews.com reported: 1.3 million scraped user records leaked online for free
In this research, we didn't attack Clubhouse users and didn't exploit any Clubhouse vulnerabilities.
Intro
Hi!
RedTeam projects have become routine for many pentest companies quite a long time ago. In Hexway, we don't do them a lot only because our main focus is our collaborative pentesting platform, Hive. But in this case, we couldn't resist - the project seemed to be very interesting.
We won't go into detail on the project itself but rather focus on one of its parts. So, in this ReadTeam testing, our goal was to compromise the computer of the CTO of a large financial organization, X corp. To achieve that, we needed the CTO to open a docx file with our payload. Naturally, the question was: what's the best way to deliver that file?
Here are some obvious options:
- Corporate email
Instead, we wanted to try something new. And that's where Clubhouse comes in.
Clubhouse? What?!
Clubhouse is a voice-based social network. It was popular for a couple of weeks in February 2021.
At that time, Clubhouse offered us a few advantages:
- Huge popularity
- Users mostly sign up with their real names, photos, and links to other social media
- It's quite easy to get into a room with interesting people, who are often hard to reach through traditional channels like email, LinkedIn, etc.
- Our experience tells us that people are suspicious of cold emails with attachments and don't open them. But in the context of an informal social platform, they seem to be less alert, which is good for RedTeam.
Here's the plan:
- Sign up in Clubhouse
- Find our target in Clubhouse
- Wait until they participate in a room as a speaker
- Join the room
- Try to engage them in a conversation. Get them interested and move the conversation over to email
- Send them an email with the attachment and payload
- The target opens our docx
- Profit!
First problems
First, we registered in Clubhouse. That was easy! We're looking for our target ... and find nothing. We couldn't find them by their name or nicknames on other platforms. Unfortunately, you can't search users by profile description or Twitter/Instagram accounts. So, they are not on Clubhouse? Maybe they have an Android? (when this article is written, 06.04.21, Clubhouse is officially available only for iOS)?
This is the way!
Okay, chin up. Our target could be using a fake name not to reveal themselves and participate in rooms dedicated to non-work-related topics. It's time to find out. Let's try to use the power of social graphs.
Here's the new plan:
- Find any X corp employee
- Get their list of followers and their accounts
- Get the list of users they follow and their accounts
- Get the lists of users of the clubs these accounts are in
- Filter all these users by "X corp" in the About profile section
- Make social graphs to find our target in someone's connections
- invitation chains (down to the first Clubhouse users)
- "following" connections
- "follower" connections
To do all that, we have to parse Clubhouse. There's no official API, so we used an unofficial API (thanks to stypr)!)
The library clubhouse-py is pretty easy to use, and we could set up a parser script in no time.
Clubhouse returns the following json in response to the API-request get_profile
Warning! To demonstrate how graphs work, we're not going to use real X corp employees' data.
{
"user_profile":{
"user_id":4,
"name":"Rohan Seth",
"displayname":"",
"photo_url":"https://clubhouseprod.s3.amazonaws.com:443/4_b471abef-7c14-43af-999a-6ecd1dd1709c",
"username":"rohan",
"bio":"Cofounder at Clubhouse ?? (this app!) and Lydian Accelerator ? (non profit for fixing genetic diseases)",
"twitter":"rohanseth",
"instagram":"None",
"num_followers":5502888,
"num_following":636,
"time_created":"2020-03-17T07:51:28.085566+00:00",
"follows_me":false,
"is_blocked_by_network":false,
"mutual_follows_count":0,
"mutual_follows":[],
"notification_type":3,
"invited_by_user_profile":"None",
"invited_by_club":"None",
"clubs":[],
"url":"https://www.joinclubhouse.com/@rohan",
"can_receive_direct_payment":true,
"direct_payment_fee_rate":0.029,
"direct_payment_fee_fixed":0.3
},
"success":true
}Example 1. Get the information about the user chipik and all of their followers and followed the accounts.
~python3 clubhouse-graphs.py -u chipik --followers --following
|------------|-----------|-------------|--------------------------------------------------------------------------------------------|----------|------------------------|---------|-----------|-----------|-----------|------------|-----------------|
| user_id | name | displayname | photo_url | username | bio | twitter | instagram | followers | following | invited by | invited by name |
|------------|-----------|-------------|--------------------------------------------------------------------------------------------|----------|------------------------|---------|-----------|-----------|-----------|------------|-----------------|
| 1964245387 | Dmitry Ch | | https://clubhouseprod.s3.amazonaws.com:443/1964245387_428c3161-1d0e-456e-b2a7-66f82b143094 | chipik | - hacker | _chipik | | 110 | 96 | 854045411 | Al Fova |
| | | | | | - researcher | | | | | | |
| | | | | | - speaker | | | | | | |
| | | | | | | | | | | | |
| | | | | | Do things at hexway.io | | | | | | |
| | | | | | tg: @chpkk | | | | | | |
|------------|-----------|-------------|--------------------------------------------------------------------------------------------|----------|------------------------|---------|-----------|-----------|-----------|------------|-----------------|Example 2. Get the list of the participants of "Cybersecurity Club"
~python3 clubhouse-graphs.py --group 444701692
[INFO ] Getting info about group Cybersecurity Club
[INFO ] Adding member: 1/750
[INFO ] Adding member: 2/750
...
[INFO ] Adding member: 749/750
Done!
Check file ch-group-444701692.html with group's users graphThat's a graph for all the group members. When hovering over a node, we see the information about the user.
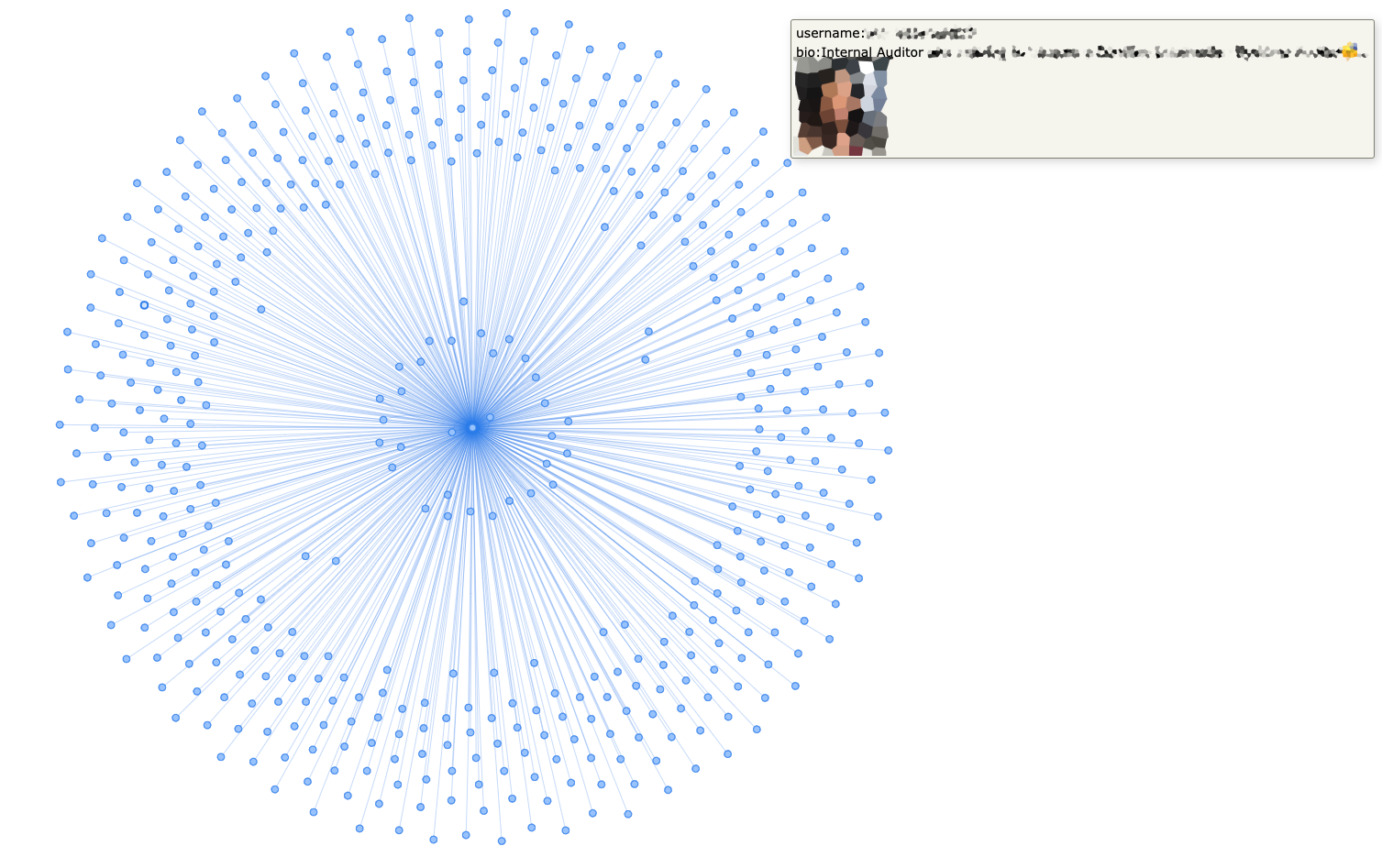
We've experimented with server request frequency to see if there are any request limits. A few times, we were temporarily blocked for "too frequent use of API", but the block expired quickly. For all the time we spent testing, our account wasn't permanently blocked.
A few days later, we had a base of 300,000 Clubhouse users somehow connected to X corp.
Now, we can search users by different patterns in their bio:
Example 3. Find all users who allegedly work/worked at the WIRED magazine and their followers and followed the accounts.
~python3 clubhouse-graphs.py --find_by_bio wired
[INFO ] Searching users with wired in bio
[INFO ] Adding 1/100
[INFO ] Adding 2/100
...
[INFO ] Adding 100/100
Done!
Find graph in ch-search-wired.html fileHere's the interactive graph with user profiles.
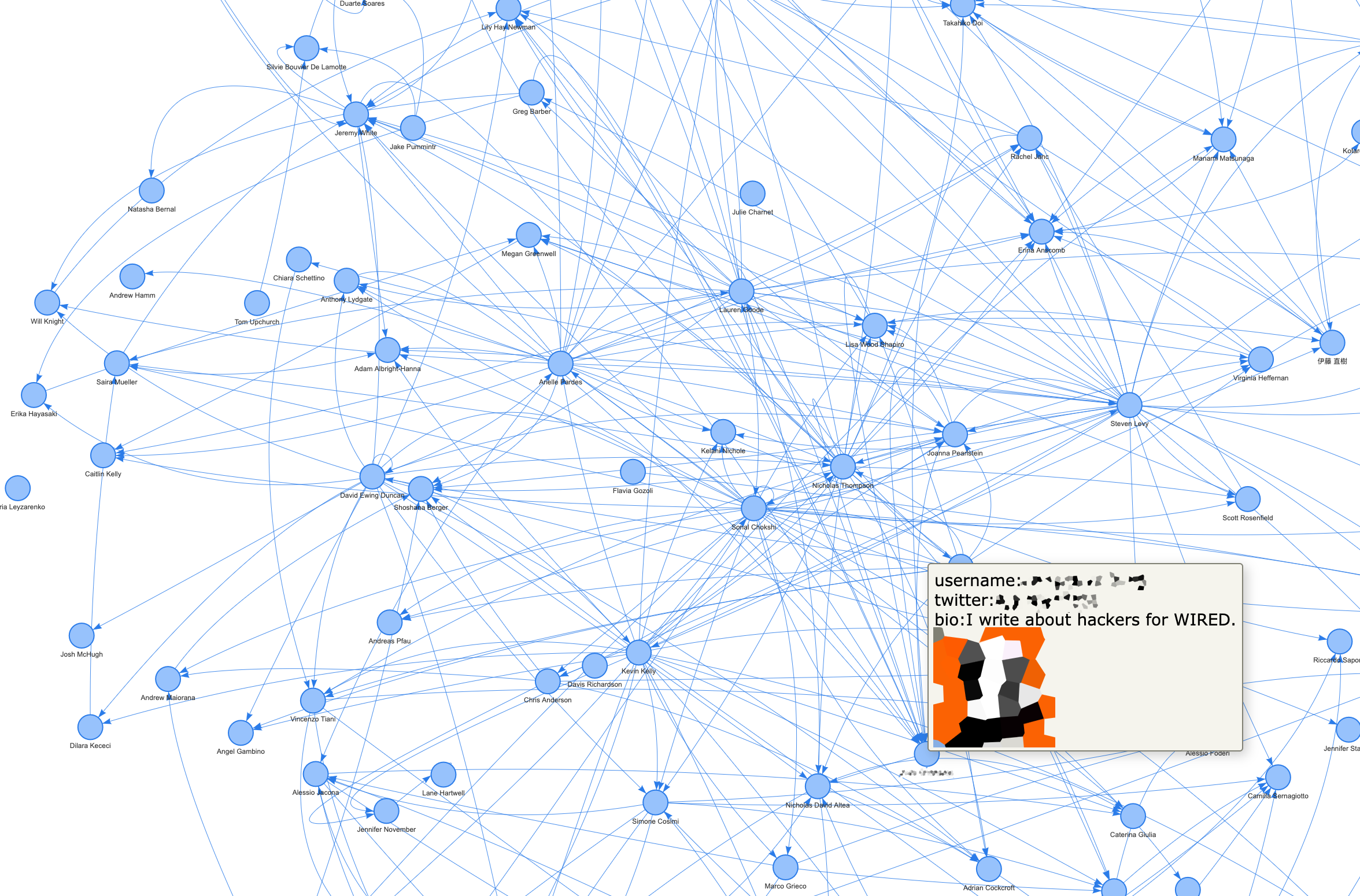
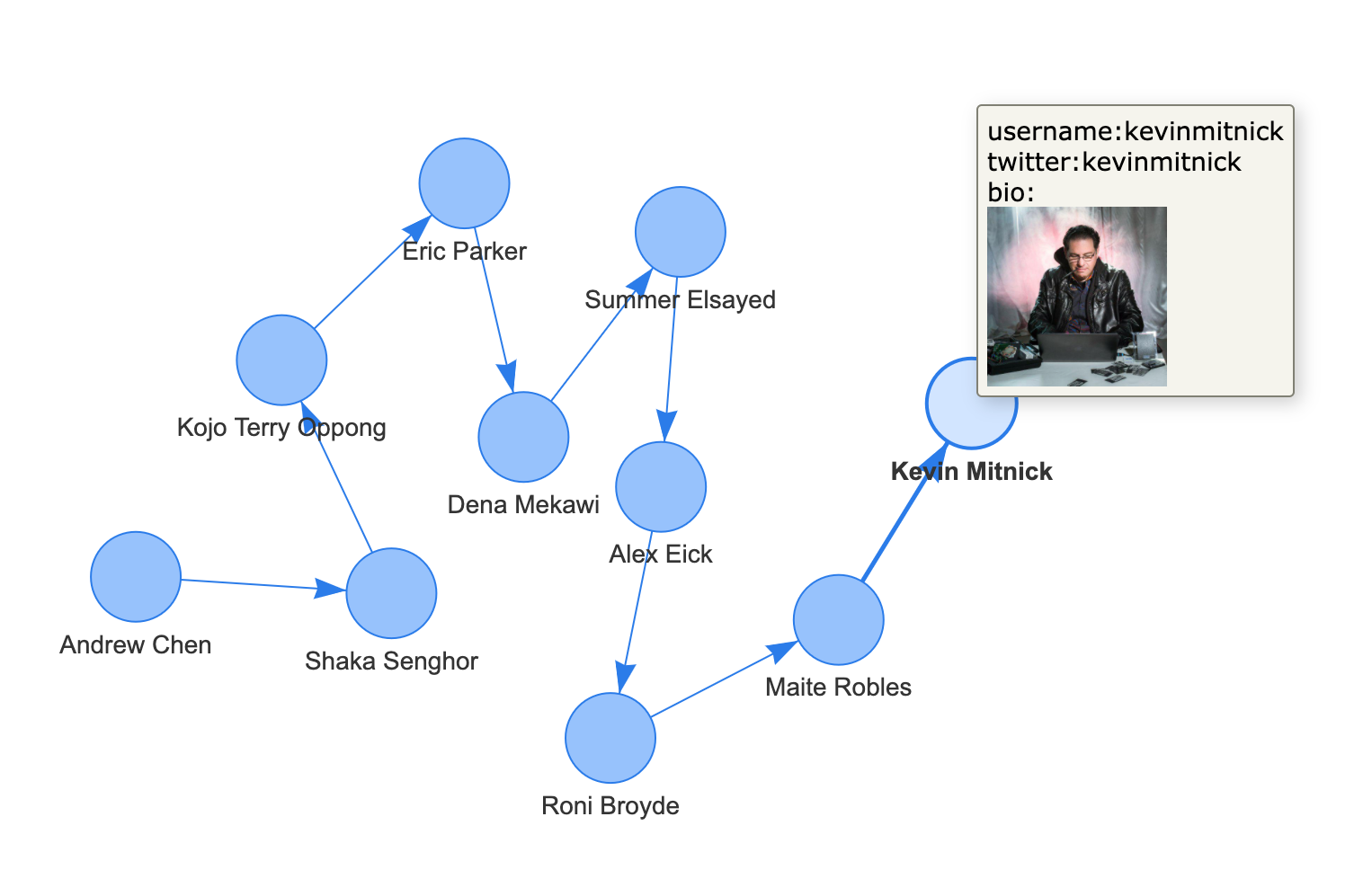
Example 4. Clubhouse invitation chain
To sign up in Clubhouse, you need an invitation from a Clubhouse user. We can use that fact as additional evidence of connections between accounts.
~ python3 clubhouse-graphs.py -I kevinmitnick
[INFO ] Getting invite graph for user kevinmitnick
Kevin Mitnick<--Maite Robles
Maite Robles<--Roni Broyde
Roni Broyde<--Alex Eick
Alex Eick<--Summer Elsayed
Summer Elsayed<--Dena Mekawi
Dena Mekawi<--Eric Parker
Eric Parker<--Global Mogul Chale
Kojo Terry Oppong<--Shaka Senghor
Shaka Senghor<--Andrew Chen
Done! Find graph in ch-invitechain-kevinmitnick.html fileHere's the interactive graph of invitations leading us to Kevin Mitnick.
Results
We collected the users, filtered them by jobs, and built a graph showing connections between them (followers, followed, invitations). Thus, we found a user with a dog on a scooter as their profile pic and no bio. This user is followed by almost all the found X corp employees but follows just one of them. Finally, the user's name contained the target's initials, so we felt safe to assume it's them.
The hardest part is done. We followed the target from one account and used another one to engage them in a conversation in some small room.
Some social engineering magic, and we got their email. After a short chain of letters, we sent them the docx with a payload. A few hours later, we got a shell on their laptop. It's done!
Takeaways
- Do not limit yourself to "standard" social engineering channels.
- Be careful with the information you put out on social media, especially if it concerns your current or previous employment.
- Most likely, the popularity of Clubhouse has passed. But there are a lot of users with real data, which can be parsed easily. All that makes us think that someone could already have collected a database of Clubhouse users, and some time later it may end up leaked.
P.S. The scripts developed during this project are available in our repository Clubhouse dummy parser and graph generator (CDPaGG)
All information is in the Description section.












