Hive 0.20.1 version. New parser engine and Metasploit & Cobalt Strike integration

New parser engine
We have completely redesigned the operation principles of our parsing system and have changed data visualization in the interface! Now, when you click on a hostname, IP, or port, the Import tab is available on the right side of the interface, which displays all the additional information about the selected element. The beauty of this panel is that it aggregates all the information about the host/port collected from various utilities. It allows you to quickly analyze the scope of work and optimize the pentest process, without scanning the same hosts several times. We have been experimenting for a long time to make it convenient for our users. We hope that you will try and like it!
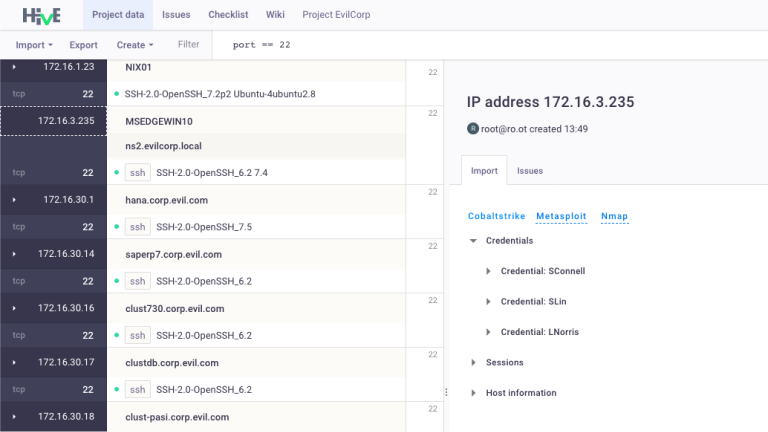
New integrations: Metasploit and Cobalt Strike
We have implemented integration with two popular tools: Metasploit and Cobalt Strike.
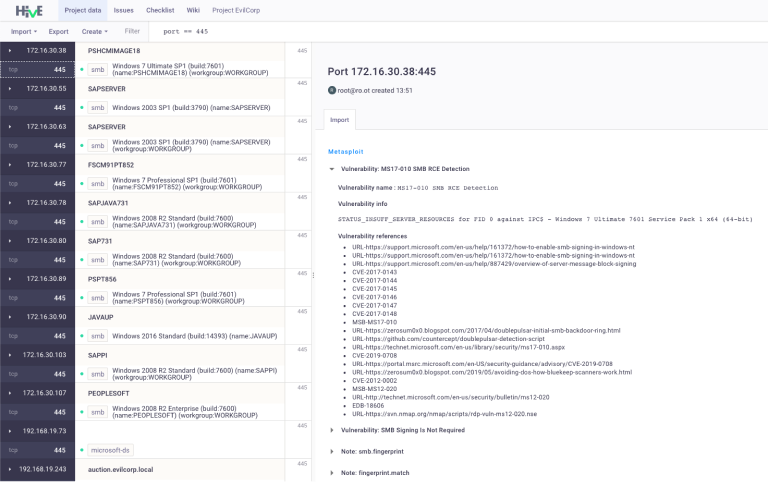
Metasploit
You can easily export a project from Metasploit to Hive. In addition to information about hosts and ports, your project in Hive will contain the data about discovered vulnerabilities, sessions, hostnames, and so on.
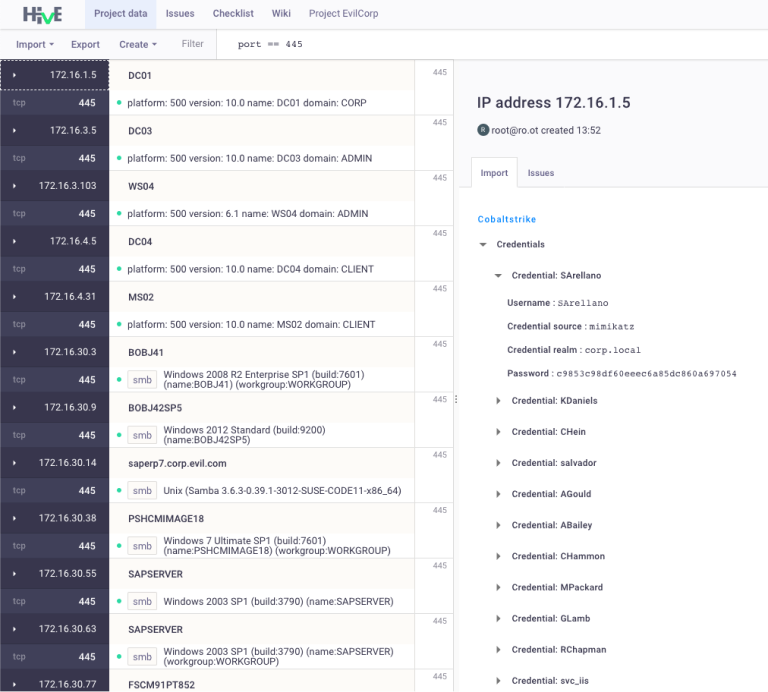
Cobalt Strike
There is another popular tool that our users have requested integration with. The exported project in Cobalt Strike is a set of xml files (services.xml, targets.xml, credentials.xml, etc). Just import them into the Hive and you will see how all the information from Cobalt Strike will be structured in an understandable view!
Other updates and bug fixes
We strive to make a solution that is not only useful for pentesters and the community but also is the easiest to use. So in this release, we have fixed a huge number of minor bugs that caused a little inconvenience to some of our users. We are getting better with every update! Thank you for that!












