Adversary Simulation: Tools and Techniques

Let’s explore emerging attack vectors and real-world threat scenarios that are being used by red teamers to simulate bad guys.
When red teamers perform their roles, they usually have permission to use any necessary approach that is possible in order to break into the organization’s systems. This allows them to perform attacks using vectors seen in real-world scenarios, used by real bad actors.
Let’s look at some techniques, tactics, and procedures used by attackers and advanced persistent threats (APTs) in the wild and from which red-teamers can use during adversary simulation activities. We also explore tools crucial in carrying out these simulations: these automated penetration testing tools can mean a world of difference in your security and pentest workflows.
Red team techniques
When APTs launch a campaign, they use various techniques at every stage of the cyber kill chain, from tried and tested techniques to novel methods. Below we explore such TTPs that can be helpful during red teaming:
Phishing
This is one of the favorite stealthy attack vectors of APTs that is seen in almost all real-world cyber attacks. A form of social engineering, phishing involves sending fraudulent emails to victims in order to make them leak sensitive information or download malware in a corporate environment.
Zero Days
Every security team has one major problem: zero days being exploited in the wild by APTs and other threat actors. Zero days are vulnerabilities that are previously unknown, meaning there are no possible detections or mitigations in the initial days, so it’s really difficult to protect against zero days.
While simulating adversaries, it might not be feasible to use zero-days (which are really tough to uncover, even more so during a red team assessment). However, the behavior can be mimicked by using a set of unpatched bugs and exploits towards them to see how well the security is.
Time Delays
APTs are very patient when it comes to performing their maneuvers. Moving from one step to another can take days or even months. For example, in one case hackers found that the victim organization’s monitoring system had logs that expired after 11 days and hence, they waited for 11 days after the initial breach before starting lateral movement, so that logs containing their footprints would expire. One popular example is the SolarWinds hack, where attackers waited over a year. This can be crucial during adversary simulation, where you can use such strategic time delays to gain an upper hand.
Ransomware
We all know what ransomware is and how devastating it has been for businesses over the years. One of the most prominent vectors in real-world cyber attacks, ransomware is a piece of malware that propagates through a network and encrypts everything. APTs and attackers then demand a ransom to decrypt important data.
While encrypting important and confidential data of your organization is recommended, ransomware can be mimicked by using automated pentesting and red teaming tools that can leave evidence that will look like ransomware to detection and monitoring tools. Setting up an isolated network with dummy data to be encrypted is also one way. The real motive is to show that software can execute code while spreading through a network.
C2 Beacons/Nodes
When an adversary breaks in successfully, they deploy command and control or C2 beacons that respond to the main C2 server for data exfiltration, to receive commands, etc. Evidence of C2 usage is pretty evident in most of the real-world cyber attacks. Cobalt Strike is one such C2 tool used heavily by APTs.
While performing adversary simulation, Red teamers can deploy Cobalt Strike beacons to mimic this behavior and see how well these communications can be detected. Not only Cobalt Strike but multiple command and control tools and techniques can be used to evade detection. Some even use DNS-based communications!
Adversary simulation tools
Multiple adversary simulation and red teaming tools are available to mimic these real-world cyber attacks and perform APT simulation, making pentests easier.
Infection Monkey
An open-source red teaming tool, Infection Monkey is a tool that can automate vulnerability discovery by spreading itself in a data center and the servers located within a data center. The infection software, called the Monkey, can perform many security assessments and propagate itself as deeply as possible in the network using whichever technique. The other part is called the Monkey Island, which can provide security data visualization regarding the agents' (the Monkeys) progress inside the network.
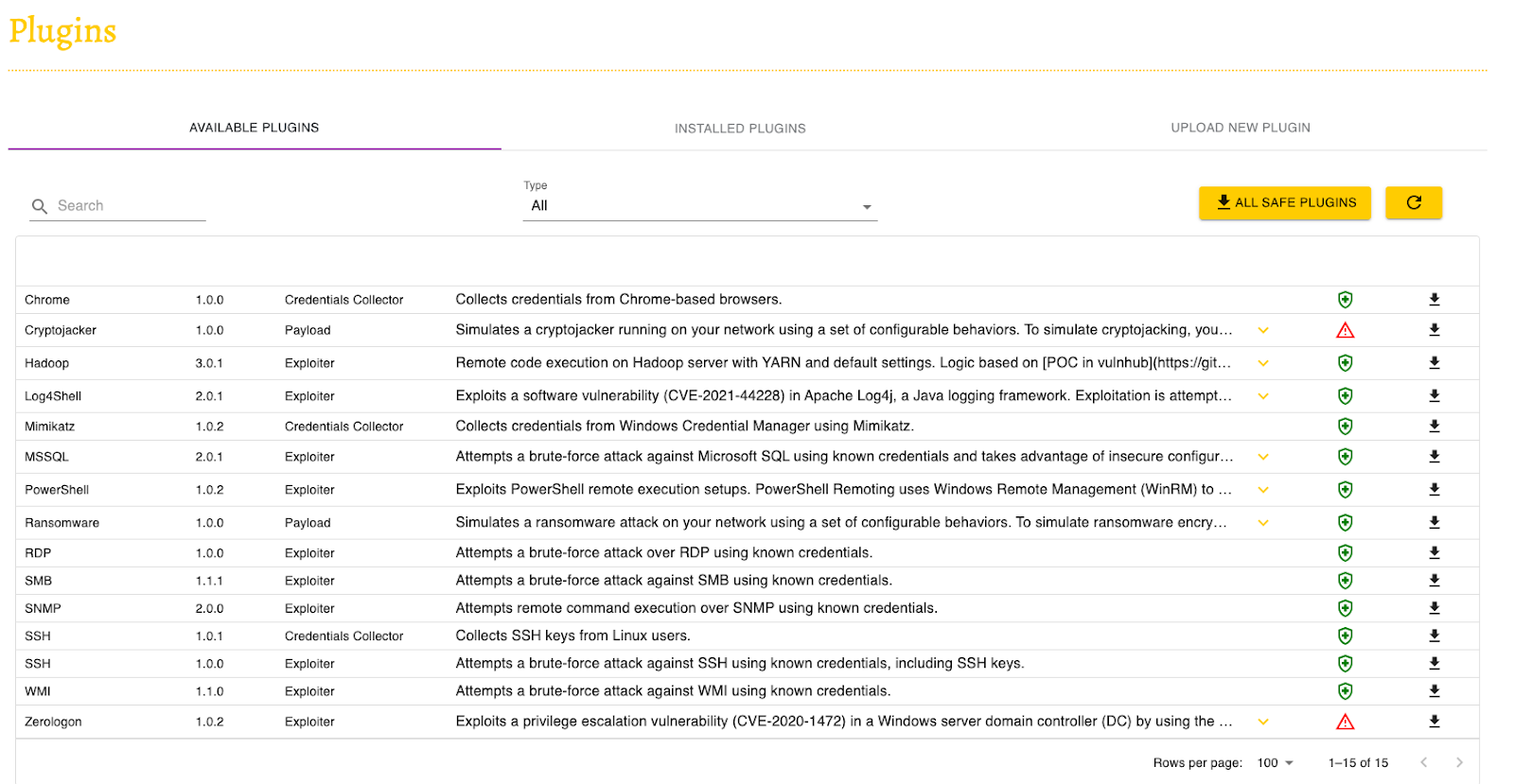
InfectionMonkey provides you with a vast array of plugins that allow you to perform different functions like exploitations, credential stealing, etc across a varied group of technologies. With granular control over configuration, InfectionMonkey can be customized as per needs.
Red Team Automation
Modeled after the MITRE ATT&CK framework, Red Team Automation is a set of scripts that tests the resiliency of an organization’s detection capabilities. RTA focuses on producing evidence and logs for multiple ATT&CK tactics so that a blue team can see how much they can detect. Instead of focusing on finding and exploiting actual vulnerabilities, Red Team Automation is more inclined towards testing how robust the detection and monitoring setup is.
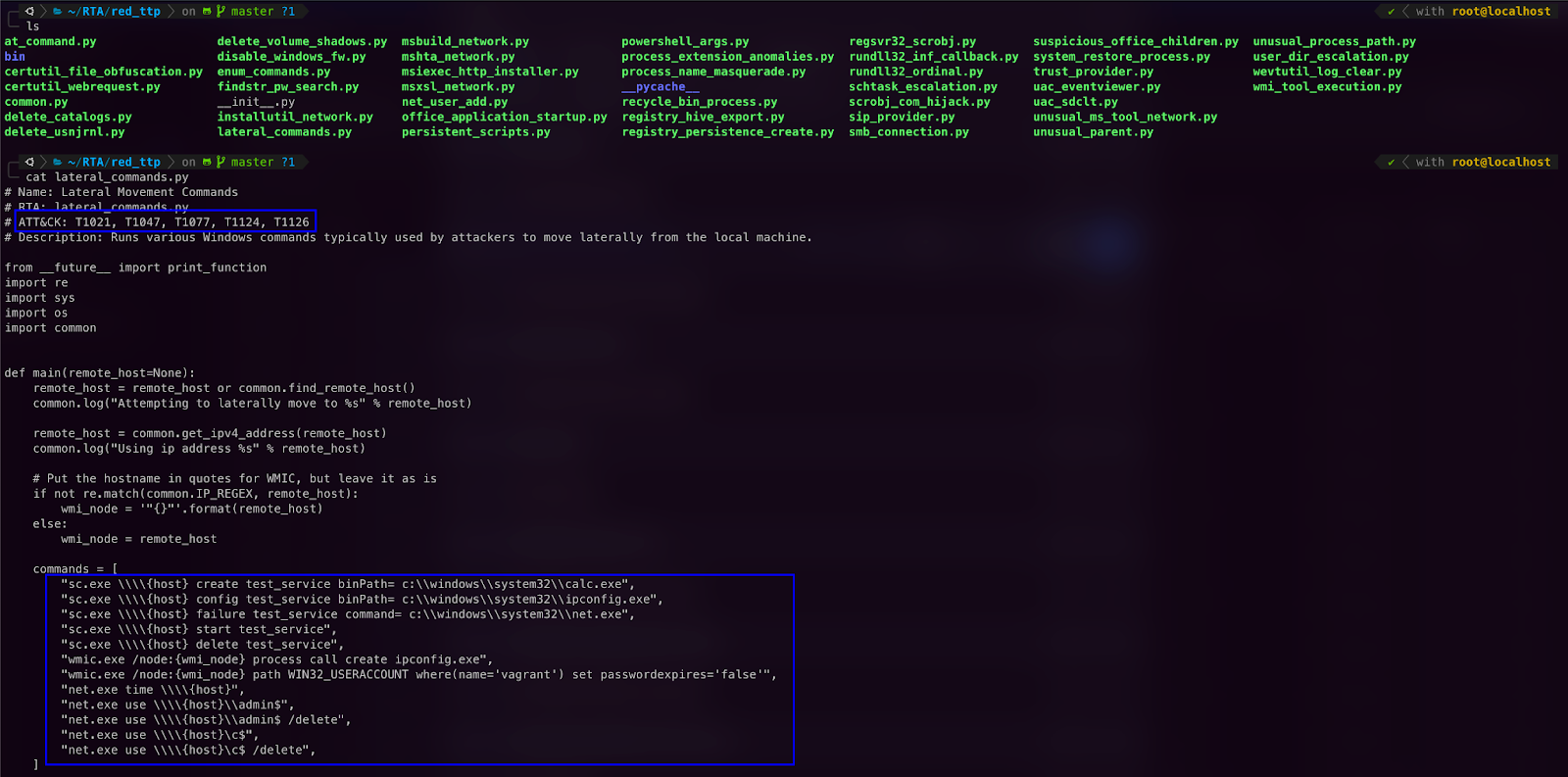
RTA has scripts for generating evidence of various malicious activities: enumeration commands, lateral movement, registry events, etc. The relevant MITRE attack IDs are also mentioned in the scripts, and you can tweak them to your needs.
MITRE Caldera
From the creators of the ATT&CK framework, Cadera is an automated adversary simulation tool that helps in manual penetration testing workflow. With a C2 system at the core and additional plugins that allow things like security data visualization, automated penetration testing to an extent, and even incident response. Other community-made plugins help with automated vulnerability discovery, network scanning, and enumeration. Easy to set up and written in Python, Caldera is one of the best tools for APT and adversary simulation.
Caldera offers a wide range of abilities that can be executed on the agents to simulate an adversary more closely. You can perform actions like bypassing AMSI, stopping everything for some time to reduce noise, changing AWS configurations, adding startup commands, and much more.
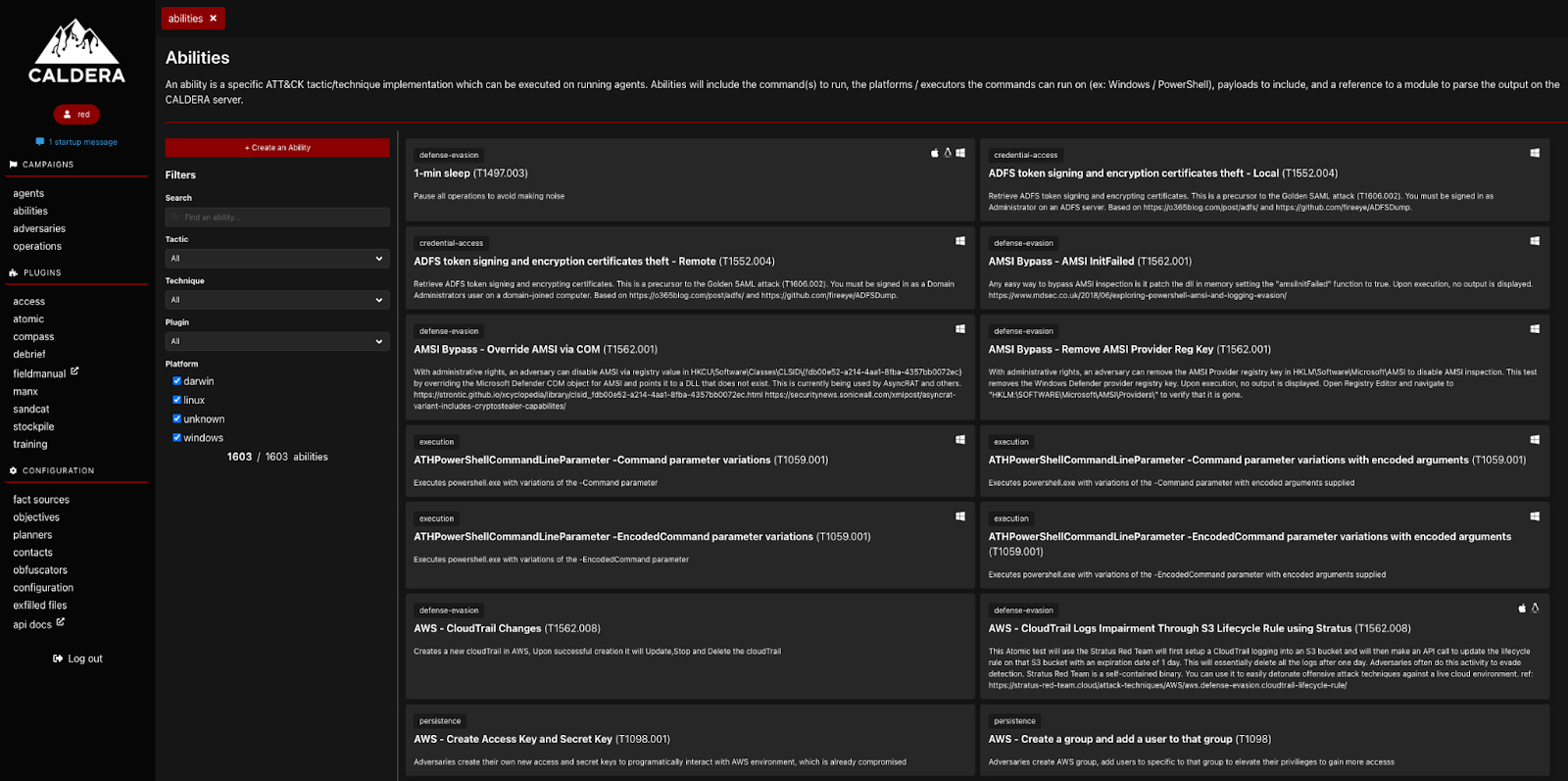
Caldera is an adversary simulation powerhouse with a wide range of plugins and configuration options.
Atomic Red Team
One of the most used and up-to-date libraries to be used by red teamers, Atomic Red Team by RedCanary is a simulation tool with focused tests so that it can be easily integrated into your pentest workflow. With a focus on automation, ART is extremely portable and has few dependencies, allowing you to execute tests on multiple environments where tests can be easily reproduced.
Stratus Red Team
If your main focus is testing and APT simulation towards a cloud environment, Stratus Red Team by Datadog should be the go-to tool. Stratus can perform automated penetration tests towards cloud environments, whether AWS, Azure, etc. It can simulate stealing credentials, automated network scanning, enumeration, deletion of logs, and many other stealthy attack vectors seen in the real world.
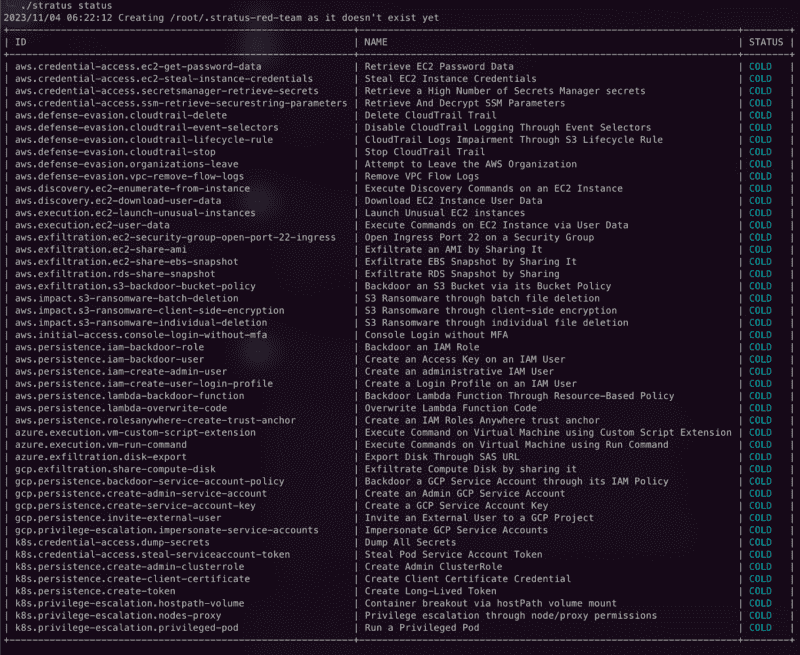
Using Stratus, you can easily keep track of the available attack IDs and which are active or not. With a vast range of available abilities, this allows easy management of the attack flow. Stratus's “warmup” feature allows you to create the required infrastructure for an attack technique without actually performing the malicious action.
Real-world cyber attacks are constantly rising, where APTs, threat actors, and other hackers develop new stealthy attack vectors, never-before-seen techniques, and zero days that prove to be a huge problem for big organizations.
Adversary or APT simulation is part of a pentest workflow or a security program that can help prepare against these threats. Whether it is checking the robustness of your detection and monitoring program or finding vulnerabilities and ways in which bad actors can exploit your systems, simulation of threat actors by red teamers can benefit any organization hugely.












