Top 7 DevSecOps Security Tools

Let's take a look at the best DevSecOps tools and utilities that can help in the efficient implementation of your DevSecOps model.
The hot topic in the product industry is DevSecOps, a junction of development, security, and operations where each of them gets equal focus during the SDLC, resulting in a product that is secure at every step, robustly built, and is maintained with consumer’s best interest in mind. Achieving all this is a complex task, but there are tools that make life easier for everyone. Let’s explore the 7 best DeSecOps tools.
- Hexway ASOC
- GitLab
- Semgrep
- Defectdojo
- Trivy
- OWASP ZAP
- MobSF
Hexway ASOC
Leading DevSecOps & AppSec platform to work with security posture in one place. Simplify vulnerability management, assess, analyze, and assign vulnerabilities, ensuring a secure and controlled environment. Hexway ASOC aggregates and orchestrates your noisy SAST/ DAST/ IAST outputs to turn them into actionable data.
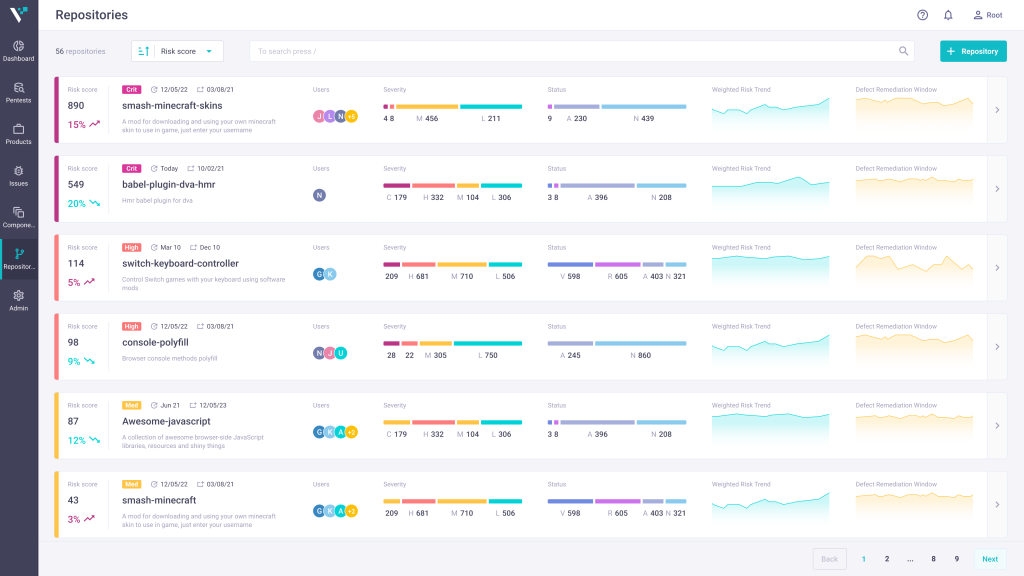
- Integration with favorite tools: Hexway ASOC integrates with commonly used scanners and tools like Nuclei, TruffleHog, Grype, and others. This allows users to speed up the process of putting security data from one place to another. Hexway doesn’t just aggregate this data in one place. It also normalizes it and converts it into data you can start working within minutes.
- Deduplication: Many scanners produce many issues. Not all of them are unique, and that’s why issue merging exists. Hexway finds duplicated issues and merges them so you can quickly work with a whole issue list without duplicates.
- Remediation control: Allows users to integrate Hexway ASOC with Jira and other task trackers to receive issues and fix them faster. Such practice not only saves time and money but also makes releases safer.
- 360 DevSecOps: Track everything in your product’s security, from remediation time to some team’s productivity. How many issues were found? How many were fixed? Long-term analytics are essential for a product’s success.
GitLab
GitLab is an all-in-one DevSecOps platform that empowers development teams to streamline their workflow with version control, CI/CD, and robust security features.
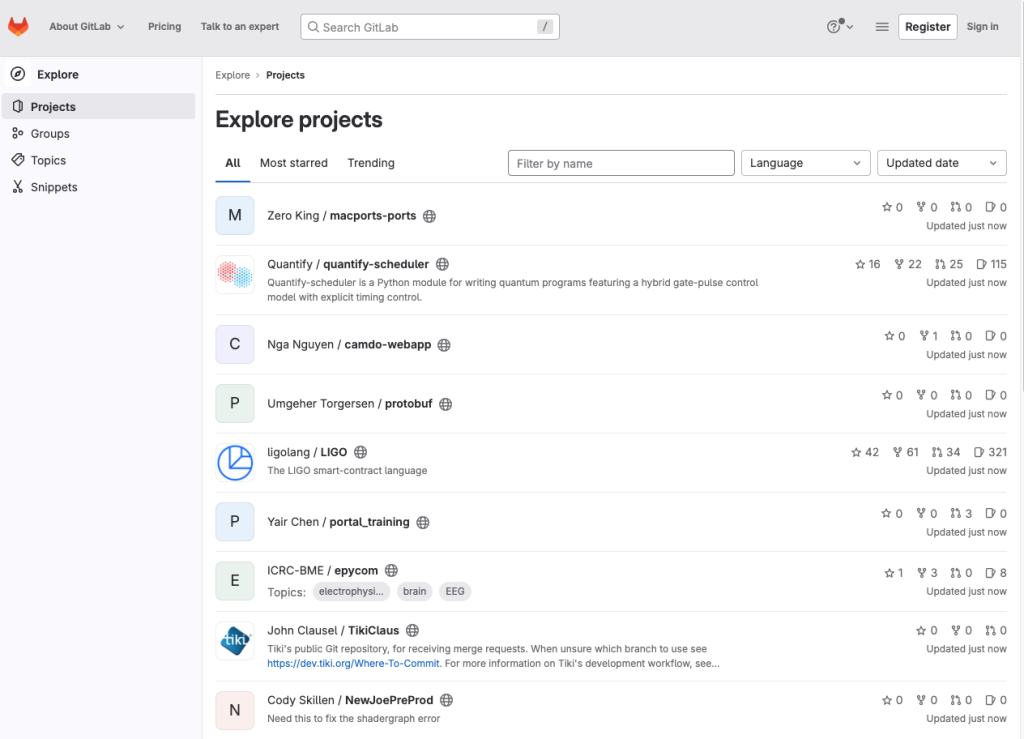
By integrating code repositories, issue tracking, and continuous integration, GitLab enables seamless collaboration and automated testing, ensuring code quality and security from the earliest stages of development. Here are some of the key features of GitLab:
- Security Scanning and Testing: GitLab provides built-in security scanning tools that can automatically detect security vulnerabilities in your code, dependencies, and container images. It includes Static Application Security Testing (SAST), Dependency Scanning, Dynamic Application Security Testing (DAST), and Container Scanning.
- Code Quality Analysis: GitLab's CI/CD pipelines can be configured to perform code quality checks, ensuring that coding best practices and security standards are followed. This helps identify potential security flaws or issues early in the development process.
- Container Security: GitLab integrates with container registries to scan Docker images for known vulnerabilities, ensuring that only secure container images are deployed.
- Secrets Management: GitLab provides a secure way to manage and store secrets, such as API keys, passwords, and other sensitive information, within the project's settings. Secrets can be securely accessed by CI/CD jobs without exposing them in plain text.
- Auto DevOps: GitLab's Auto DevOps feature allows for the automatic setup of CI/CD pipelines with built-in security scanning and testing capabilities. This simplifies the process of integrating security practices into the development workflow.
Semgrep
Semgrep emerges as a revolutionary static code analysis tool tailor-made for DevSecOps environments. With its powerful pattern-based scanning approach, Semgrep allows developers to efficiently identify and rectify security issues and bugs early in the development lifecycle. Its language-agnostic nature and extensive rules library make it a versatile choice for teams working with diverse tech stacks.
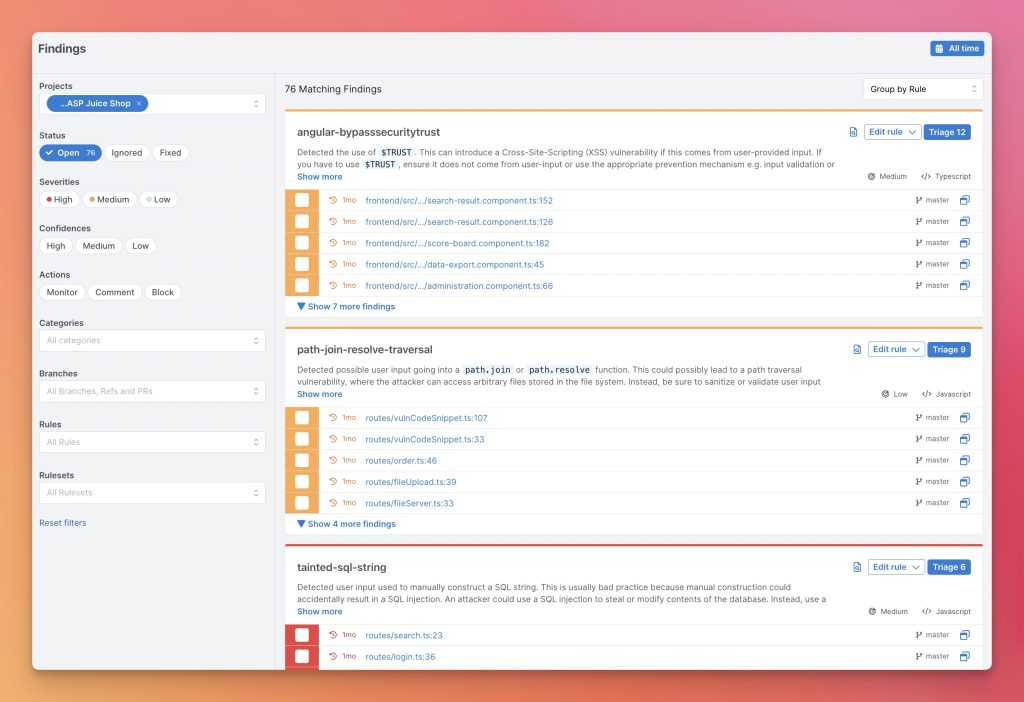
Some of the best features of Semgrep:
- Static Code Analysis: Semgrep performs static code analysis, meaning it analyzes the source code without actually executing it. This allows Semgrep to quickly scan large codebases for potential issues.
- Pattern-Based Matching: Semgrep uses a pattern-based matching system to identify potential vulnerabilities and issues in the code. It utilizes a powerful pattern language that allows users to define custom rules to search for specific patterns in the code.
- Support for Multiple Languages: Semgrep supports various programming languages, including but not limited to Python, JavaScript, Java, Go, Ruby, and others. This makes it versatile and useful for different types of projects.
- Built-in Rules: Semgrep has a set of built-in rules covering common security vulnerabilities and coding best practices. These pre-defined rules can be readily used to scan code for potential issues.
- Custom Rules: Apart from the built-in rules, developers can define their own custom rules using Semgrep's pattern language. This flexibility allows teams to tailor the tool to their specific requirements and coding standards.
- Integration with CI/CD Pipelines: Semgrep can be integrated into continuous integration and continuous deployment (CI/CD) pipelines. This means that code can be automatically scanned for issues during development, catching problems early on.
Defectdodjo
Defectdodjo, an open-source dynamic security testing platform. Defectdodjo equips developers with real-time feedback on potential security vulnerabilities to fix issues.
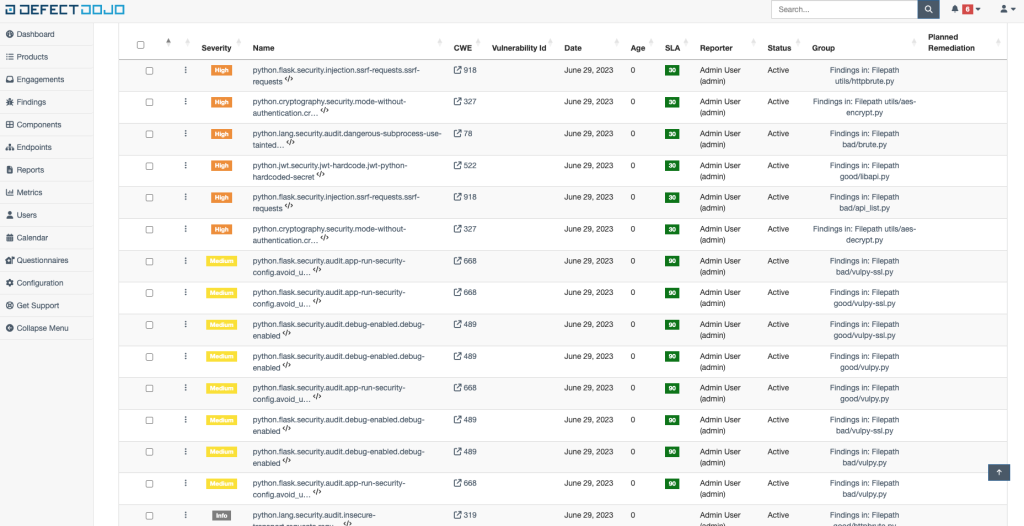
DefectDojo provides users with:
- Vulnerability Tracking: DefectDojo allows users to import and track security vulnerabilities from various security scanners, such as static analysis tools, dynamic analysis tools, and manual penetration testing.
- Integration with Security Scanners: DefectDojo supports integration with popular security scanners like Burp Suite, OWASP ZAP, Bandit, Brakeman, and many others. This enables easy import and tracking of security findings from these tools.
- CVSS Scoring: It utilizes the Common Vulnerability Scoring System (CVSS) to assess and assign severity scores to vulnerabilities based on their potential impact.
- Finding Management: DefectDojo provides a user-friendly interface for managing and organizing security findings. Users can assign findings to different users, add notes, track progress, and mark findings as false positives or verified vulnerabilities.
- Reporting and Metrics: The tool offers various reporting options to generate reports on the overall security posture of applications. It allows users to view trends, metrics, and statistics related to vulnerabilities and remediation efforts.
- Workflow Management: DefectDojo provides a workflow system to manage the process of fixing vulnerabilities. It allows teams to define custom statuses and stages to suit their internal processes.
Trivy
As containerization gains momentum, Trivy emerges as an indispensable DevSecOps tool, safeguarding containerized applications against security risks. As an open-source vulnerability scanner, Trivy analyzes container images for known vulnerabilities, ensuring that only secure and trusted images make their way into production.
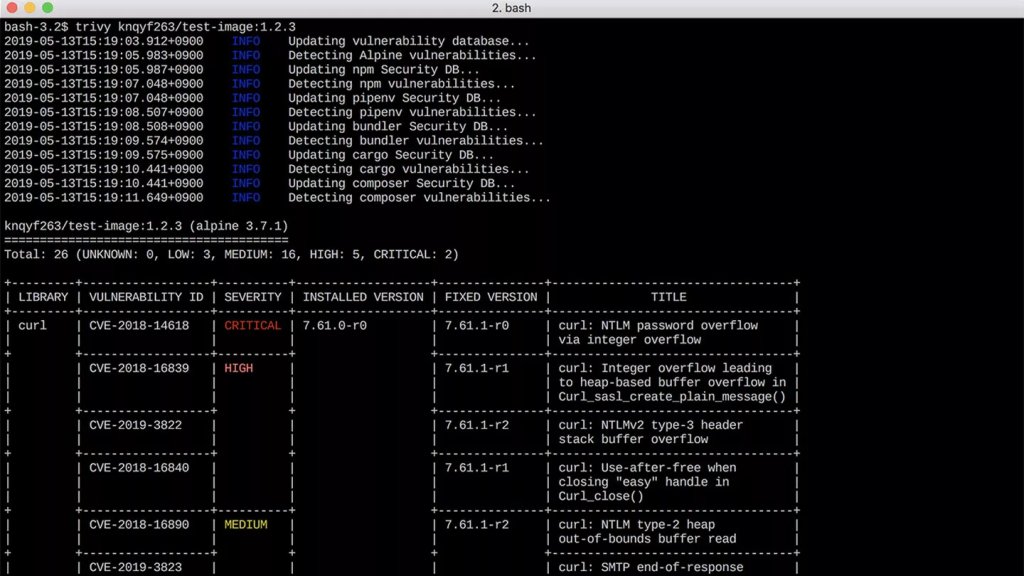
Trivy boasts a wide range of features:
- Container Image Scanning: Trivy focuses on scanning container images for vulnerabilities. It supports various image formats, including Docker images, OCI images, and others commonly used in container ecosystems.
- Vulnerability Database Integration: Trivy utilizes vulnerability databases such as CVE (Common Vulnerabilities and Exposures) to compare the components and packages within a container image against known vulnerabilities.
- Layered Scanning: Trivy employs a layered scanning approach, which means it analyzes each layer of a container image separately. This approach provides granularity in identifying vulnerabilities and their impact.
- Fast Scanning: Trivy is designed for speed, enabling quick scans of container images. This is particularly important in CI/CD pipelines, where fast feedback is crucial.
- Multiple Language and Ecosystem Support: Trivy supports scanning for vulnerabilities in a variety of programming languages and ecosystems, including Java, JavaScript, Python, Ruby, Go, and more.
- Integration with CI/CD Pipelines: Trivy can be integrated into continuous integration and continuous deployment (CI/CD) pipelines, enabling automated vulnerability scans as part of the development process.
OWASP ZAP
OWASP ZAP (Zed Attack Proxy) stands tall as a battle-tested, community-driven web application security scanner, making a resounding impact in the DevSecOps landscape. As a highly customizable tool, ZAP empowers developers to conduct thorough security assessments of their web applications, proactively identifying and remediating potential vulnerabilities.
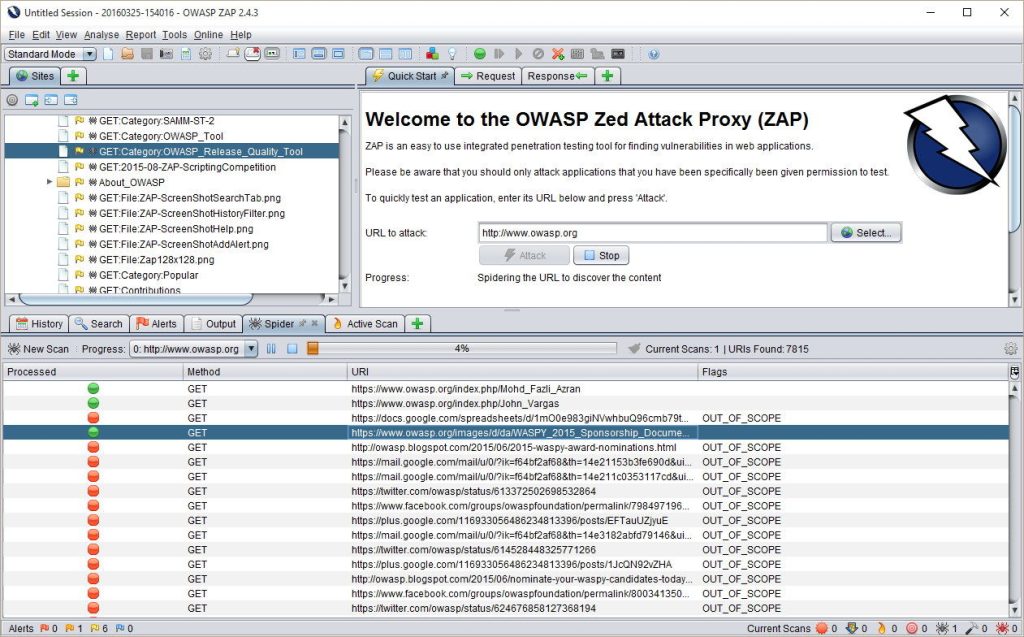
With its wide range of capabilities, OWASP ZAP can be an important tool in your arsenal:
- Active and Passive Scanning: ZAP offers both active and passive scanning capabilities. Active scanning involves actively sending requests and payloads to the target application to discover vulnerabilities, while passive scanning observes and analyzes the application's responses for potential issues.
- Automated Scanning: ZAP can automatically crawl and scan web applications to identify a wide range of vulnerabilities, such as cross-site scripting (XSS), SQL injection, security misconfigurations, and more.
- Manual Testing: ZAP provides an interactive interface that allows security testers and developers to manually explore and test web applications. This enables in-depth testing and analysis of specific parts of the application.
- Vulnerability Detection: ZAP is equipped to identify various types of security vulnerabilities, including OWASP Top Ten vulnerabilities (e.g., XSS, CSRF, etc.), authentication and session management issues, insecure configurations, and more.
- Active and Passive Proxy: ZAP can function as a proxy, intercepting and modifying requests and responses between the user's browser and the target application. This allows security professionals to inspect and modify traffic for testing purposes.
- API Testing: ZAP supports API testing, allowing users to scan and analyze the security of APIs and web services.
MobSF (Mobile Security Framework)
In the ever-evolving mobile application development realm, MobSF shines as a comprehensive DevSecOps tool tailored for mobile security assessments. MobSF offers a holistic approach to analyzing mobile apps, encompassing static and dynamic analysis while also verifying third-party libraries for potential risks.
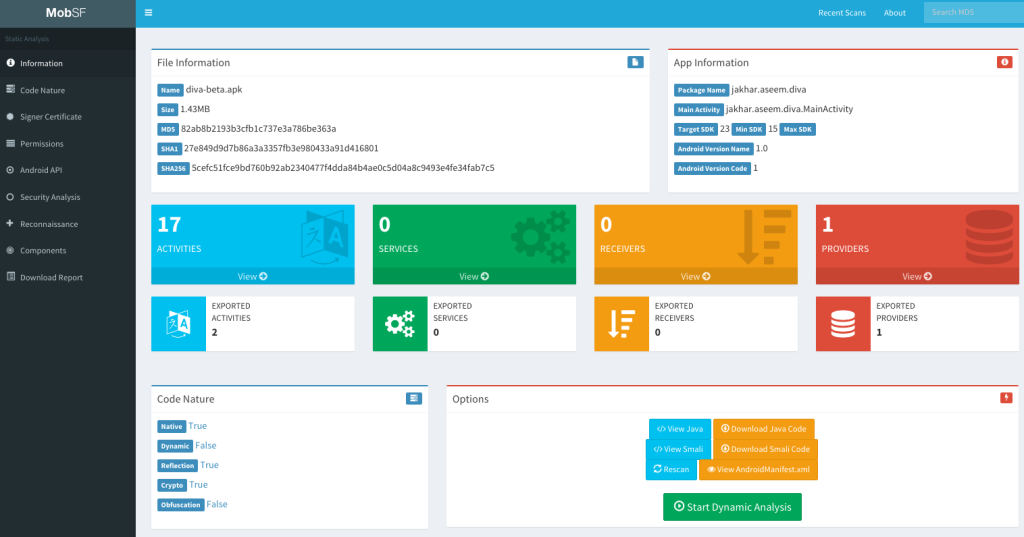
Focusing on mobile applications, MobSF provides a lot of security and automation features:
- Dynamic Analysis (Runtime Testing): MobSF can perform dynamic analysis by installing the mobile app on a real device or an emulator/simulator and interacting with it to observe its behavior and identify potential security vulnerabilities. It monitors network traffic, API calls, and system interactions to detect security issues like insecure data transmission, improper handling of sensitive information, and more.
- Static Analysis (Code Analysis): MobSF can perform static analysis on the source code of mobile applications to identify security vulnerabilities and coding issues without actually executing the app. It can identify vulnerabilities such as insecure storage, hardcoded secrets, improper permissions, and more by analyzing the app's code and resources.
- Binary Analysis: MobSF supports binary analysis of Android APK and iOS IPA files to identify potential security risks and vulnerabilities. It can extract metadata, resources, and certificates from the binary files for further analysis.
- Web API Security Testing: MobSF can scan the mobile app's web APIs to identify security vulnerabilities and weaknesses, such as insecure API endpoints, lack of authentication, and more.
- Third-Party Library Analysis: MobSF can analyze third-party libraries used in the mobile app to identify known vulnerabilities associated with those libraries.
- Reverse Engineering and Decompilation: MobSF can decompile and reverse engineer mobile app binaries to analyze their code and behavior, helping to uncover potential security issues.












