Best Penetration Testing Tools 2023

Let’s look at the most fundamental and crucial pentesting tools that help in multiple stages of pentesting, whether reconnaissance and content discovery or checking for vulnerabilities and exploitation to report and manage the data.
Nmap
Nmap, which stands for "Network Mapper," is a free and open-source utility for network discovery and security auditing. It was designed to scan large networks rapidly but works equally well against single hosts. Nmap is used by a wide range of users, from system administrators to individuals who are interested in network security and exploration.

Features:
- Host Discovery
One of Nmap's primary features is identifying network hosts. This includes identifying active hosts and the services they offer. - Port Scanning
Nmap can be used to detect open ports on a host. This is useful for understanding the attack surface of a system. - Version Detection
Nmap can also be used to determine what application and version is running on a particular port. - OS Detection
Nmap can often determine the operating system of a host. - Scriptable Interaction
The Nmap Scripting Engine (NSE) allows users to write scripts in Lua to automate various networking tasks. These scripts can make network discovery tasks more flexible and powerful. - Network Inventory, Management, and Auditing
Nmap can help network administrators with tasks such as managing network inventory, service upgrade schedules, and monitoring host or service uptime.
Nmap fits:
- System Administrators
For network inventory, managing service upgrade schedules, and monitoring host or service uptime. - Security Professionals
For identifying open ports, services running on those ports, and potential vulnerabilities associated with those services. - Network Enthusiasts and Researchers
To explore networks, understand how they work, and discover new things. - Penetration Testers
They use Nmap as part of their toolkit to understand a target's attack surface and find potential vectors for exploitation.
Nuclei
Nuclei is an open-source vulnerability scanner by the ProjectDiscovery group, which uses template-based checks against targets to find vulnerabilities and leads to almost zero false positive rates. Nuclei can scan a variety of protocols like CP, DNS, HTTP, SSL, File, Whois, Websocket, Headless, etc, and is a perfect tool for developers who are looking to keep their applications bug-free or security engineers who are engaged in pentests or bug bounty programs.

The main features of Nuclei include:
- Easy Template Creation: Templates are YAML-based and are written to perform checks for a specific vulnerability. They have a dedicated repository containing 100s of templates.
- CI/CD integration: Developers have the option to integrate Nuclei into their CI/CD pipeline, enabling continuous monitoring of their staging and production environments using personalized templates
- Fast Scanning: Written in Go and using multi-threading, Nuclei can quickly scan many hosts.
- Community Drive: Anyone can contribute to the template repository, which results in quick availability for checks against new vulnerabilities.
Hexway Pentest Suite
Hexway Hive is a self-hosted penetration testing workspace for Red Teams coupled with a customer portal tp present results to clients. It is designed to optimize each stage of security testing and provide Penetration Testing as a Service (PTaaS).
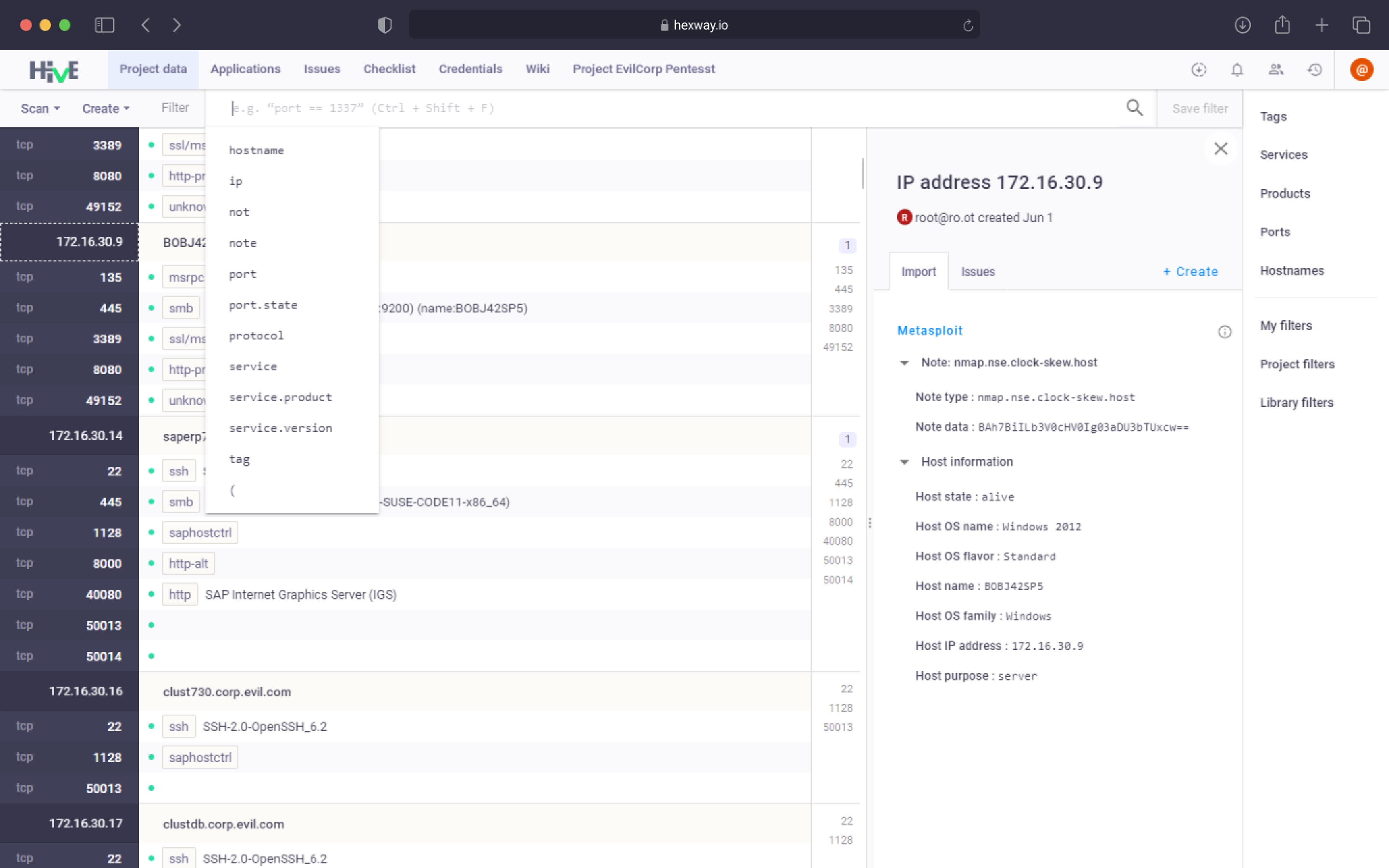
Key Features:
- Pentest Automation: Optimizing each stage of security testing helps deliver more pentests in less time.
- Integration with Security Tools: It integrates with over 20 security tools, including Nmap, Nessus, Metasploit, and more.
- Faster Reporting: It automates reporting, allowing users to focus on spotting security breaches.
- Customer Portal: It provides an additional workspace for clients to track penetration testing progress in real-time.
- Checklists & Methodologies: It provides checklists developed in a convenient way so users can follow a current methodology and never miss a task.
Collaborative Tools: It offers chats, comments, notes, and tags for efficient teamwork.
Hexway Hive is available in three plans: Community (best for freelance security professionals), Pentest (best for pentest providers), and Enterprise (best for in-house security teams).
Hexway Apiary:
Hexway Apiary is an additional workspace for Hive to present pentest results in real time and collaborate with clients or developers faster. It is designed to turn one-time clients into recurring customers with Hive & Apiary.
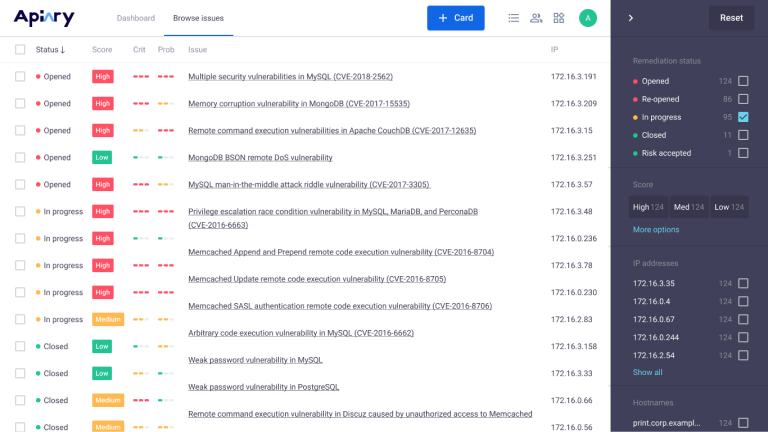
Key Features:
- Real-Time Result Sharing: It allows for easy results sharing and real-time updates.
- 360° View: It provides a comprehensive view of the security posture to protect products and track fixing progress.
- Collaboration Toolset: It offers chats, comments, and task tracker integrations for efficient communication with clients and developers.
- Secured Software: It offers OnPremise solutions, LDAP/MFA support, and internal & external software audits.
Both Hexway Hive and Apiary are designed for security teams, pentesters, and organizations that require a comprehensive platform for managing and reporting penetration testing results.
Burp Suite
Burp Suite is an internet proxy tool, mainly used for web application pentesting. With the ability to capture every request your browser makes, it lets you inspect web traffic and find vulnerabilities in it. Listed below are its strongest features:
- Capture HTTPS Traffic
Installing the custom Burp SSL certificate lets you capture and analyze HTTPS websites.
- Repetition and replay of requests
To play around with requests, the Repeater feature of the Burp suite allows you to resend a request with different parameters without needing a separate session.
- Bruteforcing
The Intruder feature provides multiple ways to brute-force different parameters, to test features like rate-limiting, password bruteforce etc.
- Community Plugins
Burp Suite has a whole load of community plugins that help enhance the existing features or sometimes even introduce new capabilities.

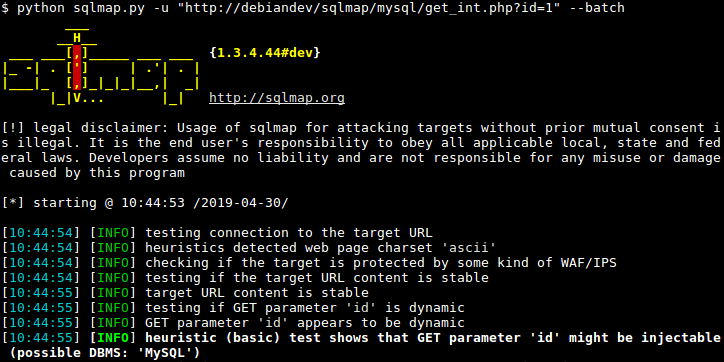
SQLMap
Simply put, SQLMap is a tool that automates SQL injection attacks. Whenever you find a URL or a request that you might think can be vulnerable to SQL injection, you can provide it to SQLMap, and it will try its best to exploit it. Let’s look at some of the features of SQLMap:
- WAF and Database detection: Sqlmap can detect if there is any WAF that is protecting the target and try to bypass it. Further, it can also fingerprint SQL database versions through error messages, etc.
- HTTP Request injection: You can provide an HTTP request in a text file, and SQLmap will try to inject payloads and see if there is any sql injection available.
- Remote command execution: In certain scenarios, sqlmap can even get a rudimentary shell through SQL injection and execute the command. One of the most popular uses is through the “xp_cmdshell” method.
A trusted tool for SQL injection, SQLmap is open source and actively in development.
Ffuf
The absolute best fuzzer out there. Directory brute-forcing or parameter fuzzing is an important aspect of pentest, in which Ffuf excels. The main feature includes:
- Fast directory fuzzing: Written in Golang, Ffuf can go through large wordlists within minutes, presenting accurate results.
- Automatic Calibration: Modern route-based applications can be hard to fuzz, but Ffuf can differentiate between a hit and a miss depending on factors like response length, number of words in response, etc. You can set these parameters manually also.
- Virtual Host Discovery: Not only directories, but Ffuf can also fuzz any parameter in the HTTP request. Whether it is a GET or POST parameter or an HTTP header. Fuzzing the “Host” header can lead to finding virtual hosts/subdomains, leading to a larger attack surface.
With a ready-to-go binary package, Ffuf (Fuzz faster U fool) is the perfect lightweight and powerful tool for all your fuzing and brute forcing needs.

Conclusion
In the ever-evolving world of cybersecurity, pentesters rely on many tools to assess and fortify their clients' defenses. As we explored the top pentesting tools of 2023, it became evident that they continue to mature and adapt, reflecting the evolving threat landscape. As the landscape evolves, pentesters must stay vigilant and innovative, leveraging these and many other tools and embracing emerging technologies to stay one step ahead of malicious actors.












