Why PTaaS is Evolving the Level of Pentest Quality?

The attackers have evolved and are stronger than ever. This has forced vendors to up the security services they provide, and PTaaS is that game changer, pushing the quality of pentests to the next level. Let’s take a look at how PTaaS achieves this.
Why it is important to improve pentests quality?
By the end of April, more than 900 CVEs were published already. The threat landscape is so dynamic and fast-paced you might patch ten bugs today and be vulnerable to 10 more the next day. It’s a never-ending game.
That’s why there is a dire need for improved pentest practices and methodologies, as proceeding with the older ways of pentest is equivalent to putting your organization at risk. Also, it becomes difficult to go head-to-head with competitors as they evolve their pentest methodologies to be ahead in the game. And PTaaS is that player that changes the whole culture around how providers do pentest and build better communication with a client and collaborate inside the team more effectively. We will explore where the traditional pentest approaches fall short in today’s attack atmosphere and how PTaaS improves pentest by giving a comprehensive experience with more accurate results.
What's wrong with the traditional approach?
Several aspects of traditional and older penetration processes were limited in nature. Understanding these shortcomings is important before looking at how PTaaS improves them.
Short testing period
Traditional pentesting is usually a one-time affair, where organizations have vendors perform pentests over a small period of time, sometimes for compliance purposes. This only provides protection against the existing vulnerabilities and presents an overview of the company’s security posture for that period of time, failing to provide ongoing visibility and continuous protection from new and emerging threats.
Reporting pitfalls
Traditional reporting methods are limited, with the inability to provide well-structured reports. It is usually provided at the end of the pentest period, during which the organization stays unaware of the findings. The lack of ongoing communication between testers and developers makes it hard for organizations to apply quick mitigations. Further, the presented reports are not comprehensive, and vulnerabilities are just reported without context, making it difficult for developers and blue teamers to understand the situation and put necessary fixes on time.
Lack Of Automation
Manual tasks were the focus of older processes: whether it was parsing data from one tool to search. That meant everything was done through human intervention: gathering data, importing data, generating reports, status updates, etc. The lack of scheduled scans meant relying on human intelligence for the smallest of misconfigurations. This led to time-consuming pentests with higher chances of error occurrence, which can even consequentially make the business lose customers’ trust, and in the worst case, lose the client itself.
Less Cost-Effective
We’ve already discussed how earlier pentests were a one-time event, and these were expensive engagements. Vendors usually ask for a heavy amount just to do a sloppy pentest over a limited scope. No continuous monitoring, actionable reports, easier glance at data and attack surface, etc. Hence, they proved to be less feasible and overpriced compared to what PTaaS provides.
Insufficient Collaboration
One of the major cons of older methodologies was the disconnect between teams, leading to a major lack of collaboration. When there is a lack of internal messaging, timely discussions, and information exchange but different parties are involved, etc it makes the pentests tougher for both the client and the pentesters. Proper collaboration ensures timely fixes, and a better understanding of the application by the pentest team, and the same goes for the developers and blue teams, as they are able to grasp the nature of bugs better. All in all, collaboration makes pentest a smoother and more efficient experience.
This list is by no means exhaustive. Alongside the major things discussed above, there was the issue of limited scope and flexibility, difficulties in integrating the pentest engagements into existing workflows, and multiple other limiting factors.
How PTaaS can improve the quality of pentesting
The above-mentioned points left gaps in the security posture of organizations. Pentest-as-a-service aims to improve the quality of pentests by solving the problems posed by traditional methods of pentesting.
Continuous Pentest
Unlike being a single event taking place annually, pentesting has become an ongoing affair. PTaaS lets you set up continuous monitoring, scheduled scans, periodic manual pentests, etc to keep the security posture up to date with the fast-moving threat landscape. This ensures that a tight check is provided all around the year.
Routine Automation
PTaaS relies heavily on automation. Multiple phases and tasks involved in pentests become repetitive after a point. Automation takes these monotonous tasks and lets you use the arsenal of automation tools to perform them faster with less interaction. Things like scheduled scans, report generation, etc can be offloaded while you focus on things that are more important, like looking for security breaches.
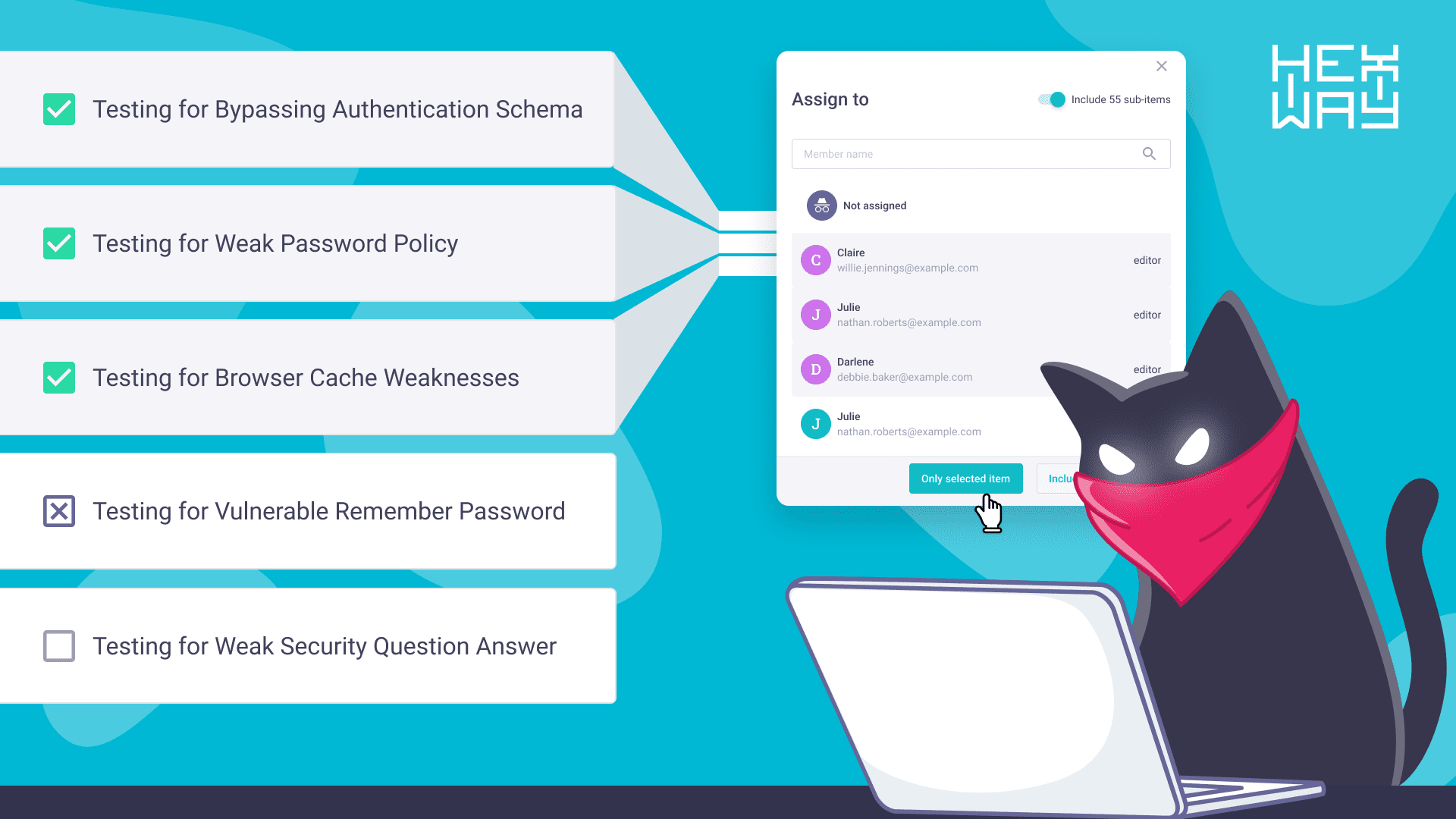
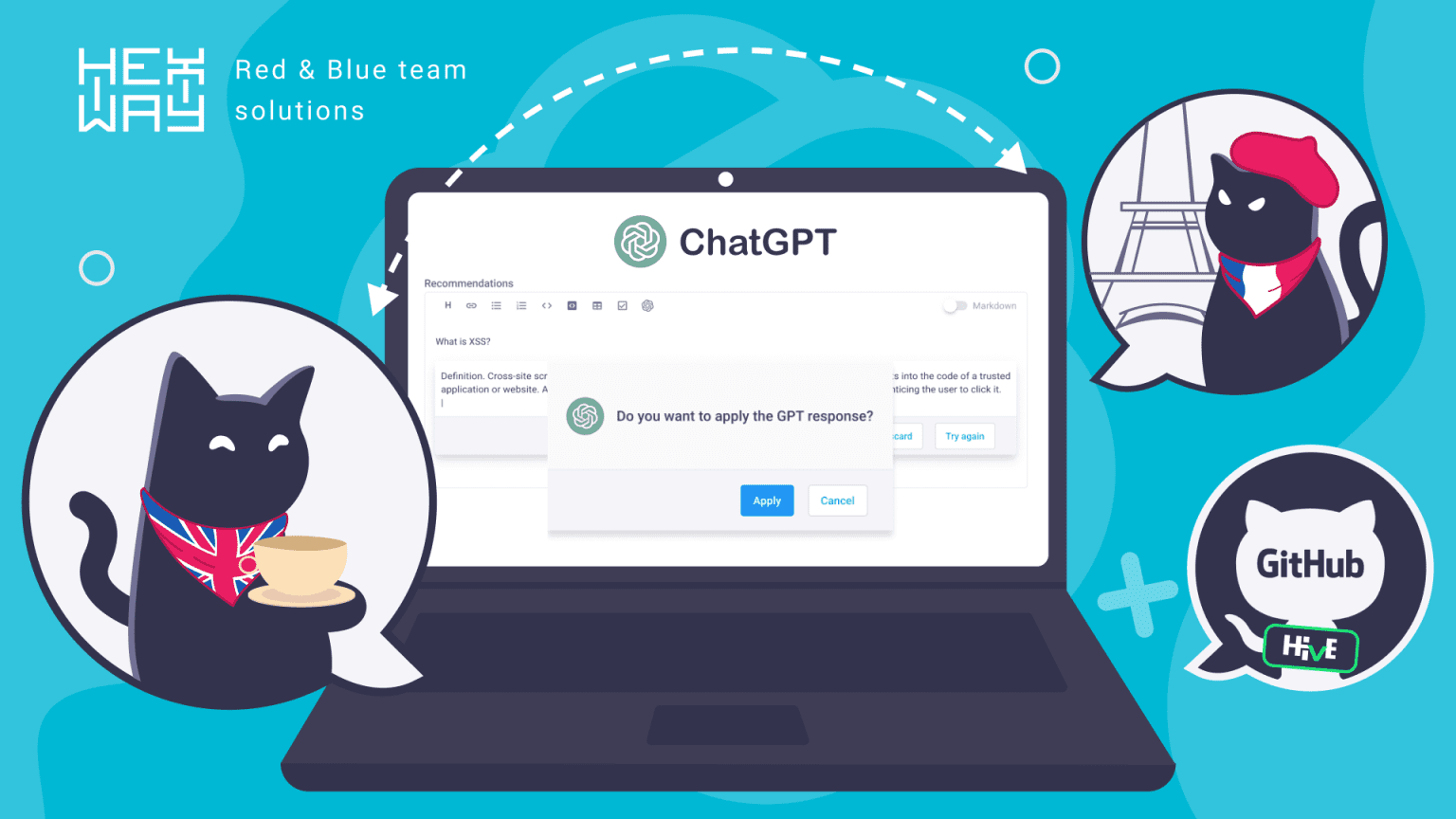
Better Communications
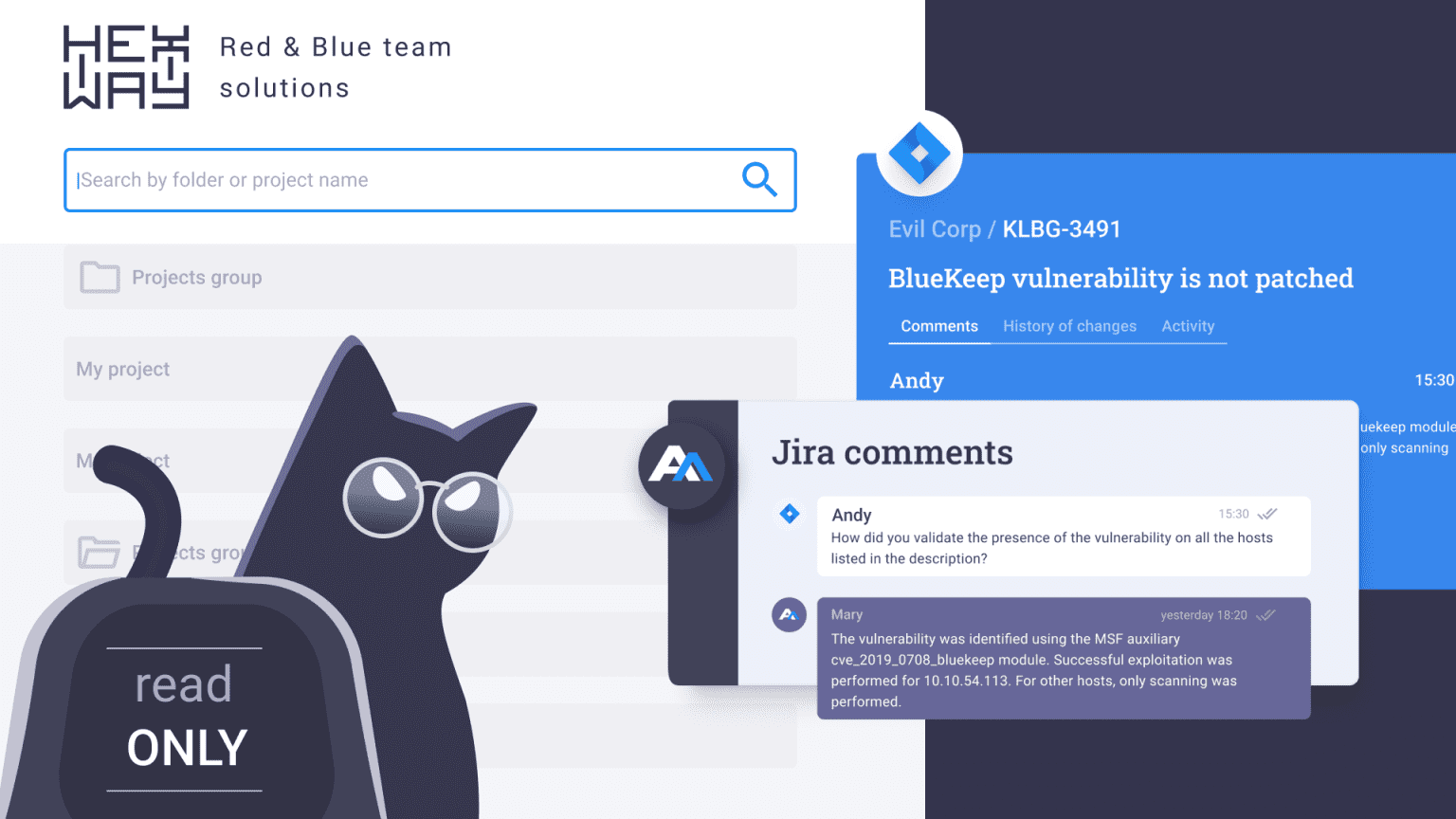
PTaaS providers ensure that their platform is built in such a way that allows real-time and productive communications between testers, blue teamers, developers etc. Tools like Hexway’s Hive and Apiary make sure that updates, bugs, and issues are relayed to clients instantly with contextual information so that it is effectively used to fix the issues. Features like JIRA integration with reverse synchronization are extremely helpful in creating tasks and tracking the status of issues.
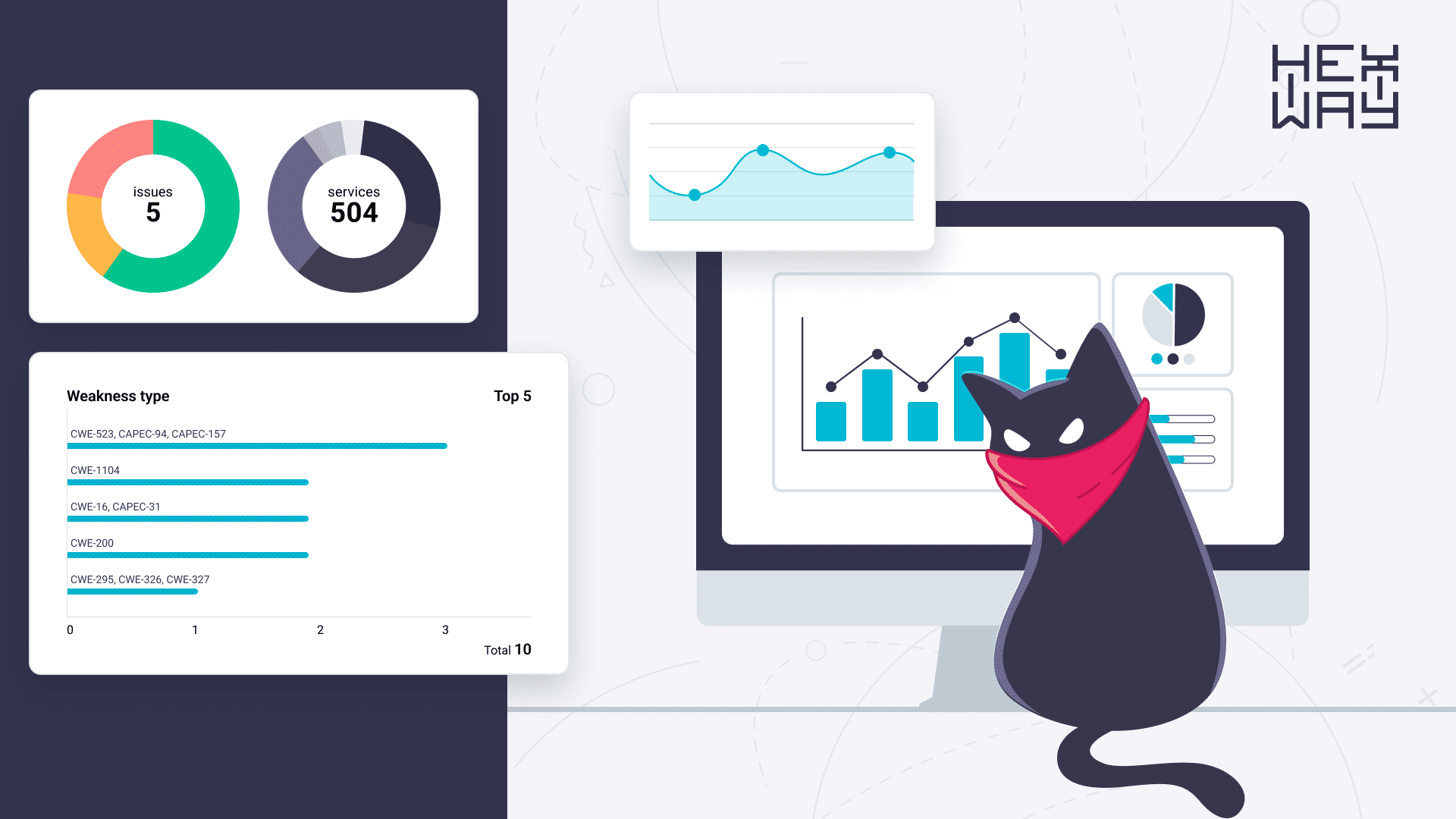
Better Reports
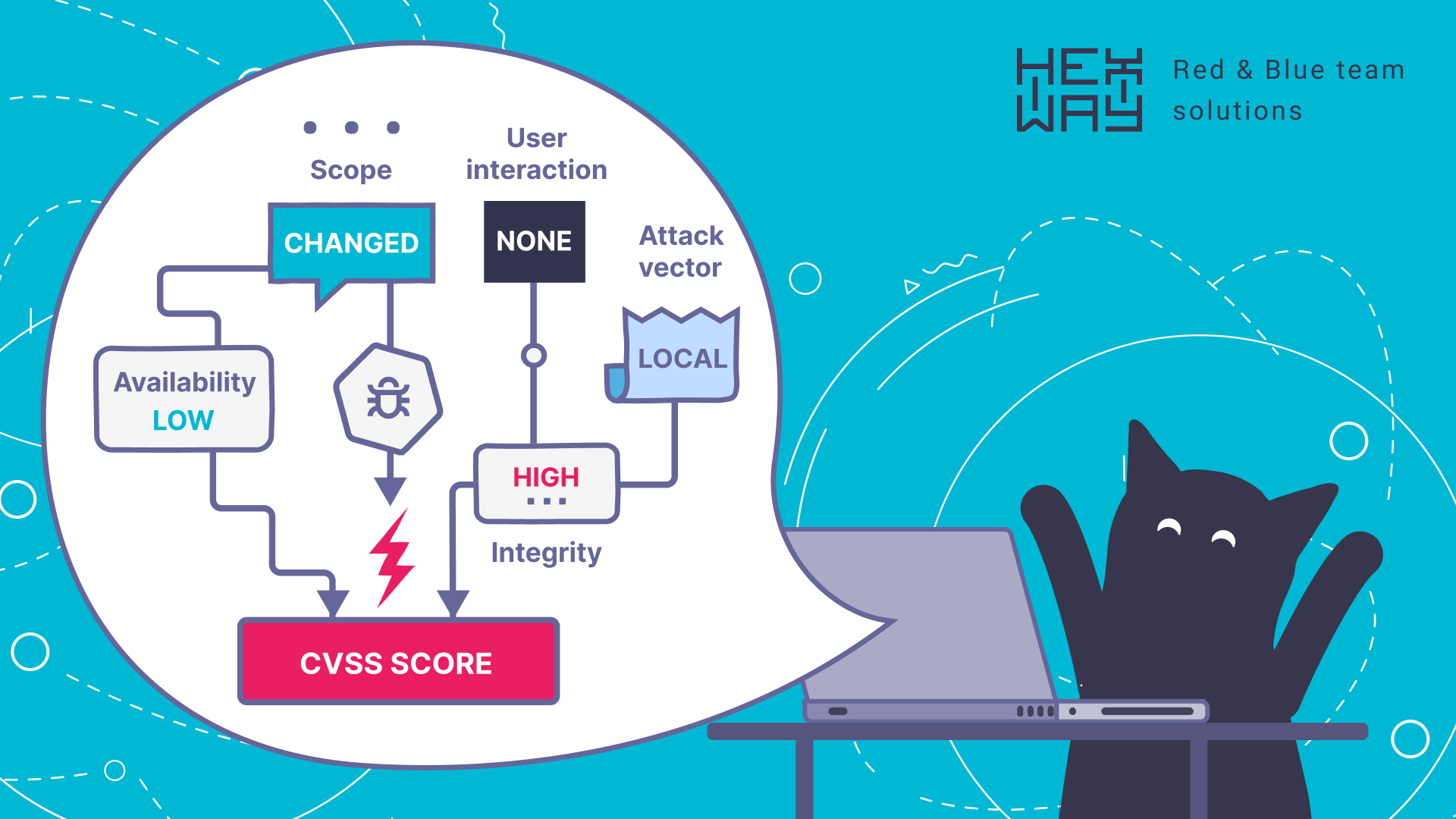
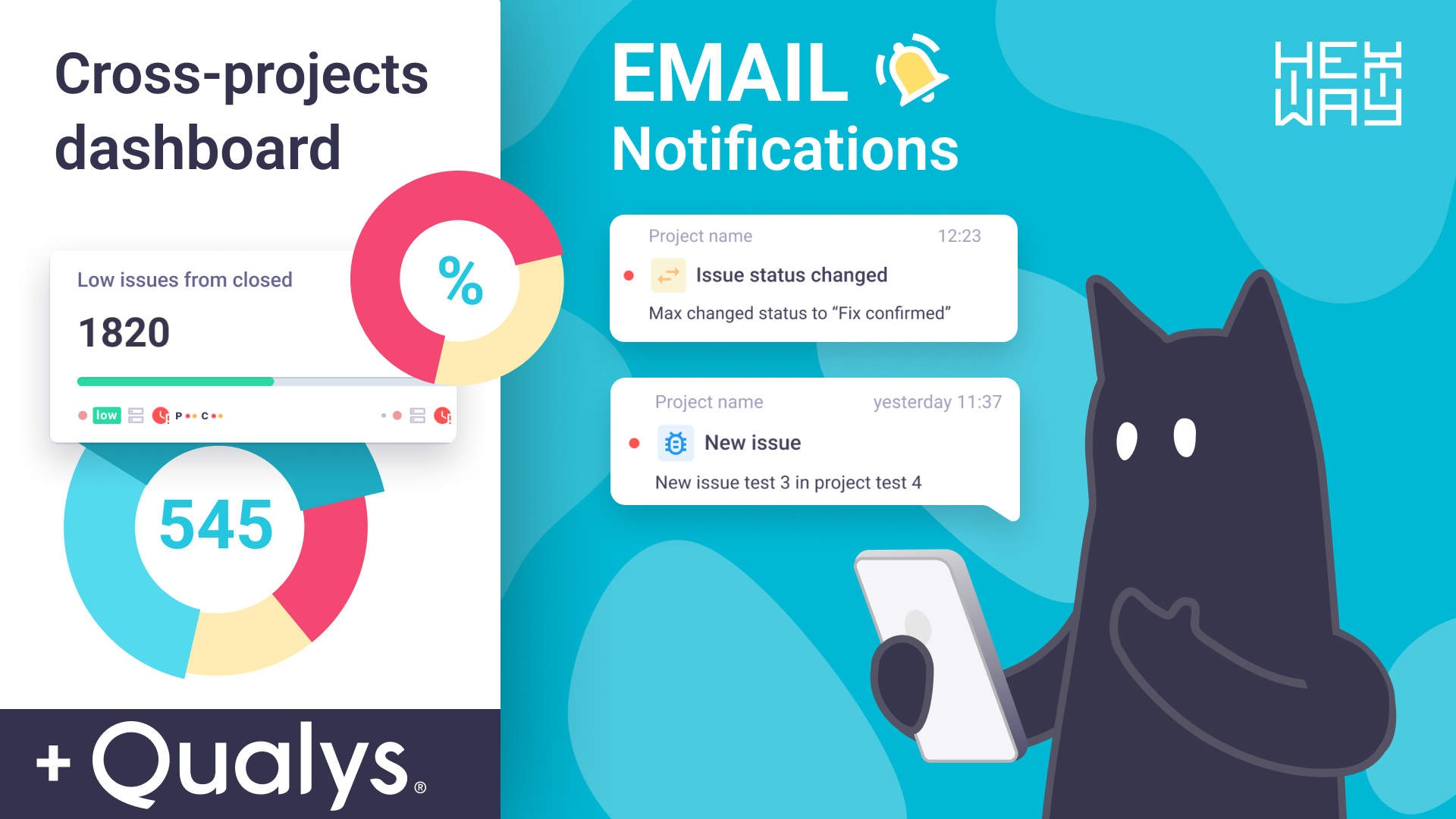
The purpose of reporting is to provide actionable data which is enriched with structured information. This lets clients deeply understand the state of their security infrastructure and where it needs strengthening and take action on fixing found bugs. PTaaS platforms provide highly detailed reports alongside what mitigation and good practices are required. Graphs, visualization, etc let the organization know the overview of the posture and make better security-oriented decisions.
These improvements over the existing and traditional pentest processes allow PTaaS to provide an overall more comprehensive testing experience. This, combined with how everything is centrally managed and high levels of precise testing due to the pool of talented security experts and strong collaboration between multiple teams involved, leads to pentests that are not only technically advanced but pentests that are of higher accuracy.
Successful PTaaS implementations
Let’s take a few scenarios in which organizations can benefit from PTaaS implementations by pentest vendors.
- Application Security Testing: A large financial institution wanted to ensure the security of its online banking application, which processed millions of transactions daily. They partnered with a PTaaS provider who conducted regular penetration testing to identify and remediate vulnerabilities in the application's code, database, and network infrastructure. The result significantly reduced the risk of data breaches, improved regulatory compliance, and increased customer trust.
- Network Security Testing: A multinational manufacturing company wanted to secure its global network infrastructure, which consisted of multiple data centers, offices, and remote sites. They worked with a PTaaS provider who performed regular network penetration testing to identify and mitigate vulnerabilities in their firewalls, routers, switches, and other network devices. The result was a more secure and resilient network infrastructure, reduced risk of cyber attacks, and improved business continuity.
- Cloud Security Testing: A fast-growing technology startup wanted to ensure the security of its cloud-based infrastructure, which hosted its applications, databases, and data analytics tools. They partnered with a PTaaS provider who conducted regular cloud security testing to identify and remediate vulnerabilities in their cloud infrastructure, configuration, and access controls. The result was a more secure and compliant cloud environment, reduced risk of data breaches, and improved agility and scalability.
- IoT Security Testing: A large healthcare provider wanted to secure its network of medical devices, which included patient monitoring systems, infusion pumps, and other IoT devices. They worked with a PTaaS provider who conducted regular IoT security testing to identify and mitigate vulnerabilities in the devices' firmware, software, and network connectivity. The result was a more secure and reliable medical device network, reduced risk of cyber attacks, and improved patient safety.
In summary, PTaaS implementations can bring a wide range of benefits to organizations, including improved security posture, reduced risk of data breaches, better compliance with regulatory requirements, increased customer trust, and business continuity.
Conclusion
There is no denying PTaaS has raised the bar for pentests The introduction of continuous testing, automation, scalability, and smooth integration into existing workflows leads to accurate testing of an organization's systems and infrastructure. Not only this, these factors allow pentesters to improve the quality of their penetration tests by delegating routine and repetitive tasks to tools, allowing them to focus on more critical aspects of the testing process, resulting in better security professionals as they can spend time honing their skills.
Additionally, PTaaS enables organizations to receive detailed and context-rich reporting, helping them prioritize and remediate vulnerabilities more effectively and allowing pentesters to perform accurate and precise pentests, covering large asset scopes resulting in higher quality. All of this makes PTaaS and the resulting pentests an essential part of any organization’s security needs. Hexway's PTaaS tools, Hive and Apiary, are specifically designed to help organizations and pentest providers improve the quality of their penetration testing by providing an all-in-one solution for collaboration, data management, and more! You can check out the online demo or download both workspaces for a self-hosted version to experience the benefits of these powerful PTaaS tools firsthand.